- By Bogdan Popa
- July 26th, 2017

Virus Takes Over Third-Party Android Store, Serves Malware for First Download
Security firm ESET discovers malware in third-party store
- By Bogdan Popa
- November 25th, 2016
Cybercriminals Spread Malware Using Microsoft’s OneDrive
New way found to make malware links look legitimate
- By Catalin Cimpanu
- October 30th, 2016

Problems Reappear for IoT Device Owners with Discovery of New DDoS Trojan
Security researchers discover IRCTelnet malware
- By Catalin Cimpanu
- October 30th, 2016
RAT Hosted on PasteBin Leads to BSOD
Terminating malware's process leads to BSOD
- By Catalin Cimpanu
- October 28th, 2016
The Super-Dangerous Rex Botnet Has Only Around 150 Bots
Rex incorporates some features from the Mirai malware
- By Catalin Cimpanu
- October 27th, 2016
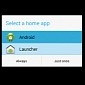
Android Ransomware Gets Around Auto-Start Restrictions by Hiding as Launcher App
Newest trick in Android.Lockscreen's playbook
- By Catalin Cimpanu
- October 27th, 2016

Hungarian Developer Most Likely Behind Hucky Ransomware
New Locky clone discovered by Avast researchers
- By Catalin Cimpanu
- October 25th, 2016

GM Bot Banking Trojan Can Now Bypass Android 6 Security Defenses
New GM Bot Android banking trojan version discovered
- By Catalin Cimpanu
- October 24th, 2016
Locky Adds Support for a New "S**T" Extension
New spam campaign has made victims all over the world
- By Catalin Cimpanu
- October 23rd, 2016
Malware Authors Adopting the Freemium Model Spells Bad News for the Rest of Us
New phishing campaign detected spreading Viotto Keylogger
- By Catalin Cimpanu
- October 21st, 2016

FakeFile Trojan Opens Backdoors on Linux Computers, Except openSUSE
Trojan targets desktops, not servers or IoT devices
- By Catalin Cimpanu
- October 20th, 2016
VoIP Gaming Servers Abused to Spread Remote Access Trojans (RATs)
Activity heightens from NanoCore RAT campaigns
- By Catalin Cimpanu
- October 18th, 2016

Hajime IoT Worm Considerably More Sophisticated than Mirai
New threat surfaces on the IoT landscape
- By Catalin Cimpanu
- October 16th, 2016

TrickBot Shows Strong Connection to Old Dyre Banking Trojan
Researchers find traces of Dyre in new TrickBot trojan
- By Catalin Cimpanu
- October 16th, 2016

Exotic Ransomware Author Tries to Be Friends with Security Researchers
Ransomware author is more interested in making friends rather than writing a professional ransomware
- By Catalin Cimpanu
- October 14th, 2016

Android Trojan Asks Victims to Submit a Selfie Holding Their ID Card
Social engineering tactics hit a new level
- By Catalin Cimpanu
- October 14th, 2016

A New Linux Trojan Called NyaDrop Threatens the IoT Landscape
Malware author returns to IoT landscape following Mirai's success and the wealth of vulnerable devices