A new ransomware appeared this past week, and in the span of two days, it went from version 1.0 to 3.0, as its author, a German developer known as EvilTwin, or Exotic Squad, really wanted to impress security researchers with his "work of art."
Called Exotic, this ransomware is your run-of-the-mill ransomware that locks files, shows a ransom note, and asks for money to unlock your data.
According to MalwareHunterTeam, the developer who first spotted the ransomware, this is not the most advanced and well-coded piece of malware he has looked at in the past months.
Exotic isn't a threat at the time of writing. According to multiple researchers, and its author, the ransomware is still a work in progress.
Ransomware author wants to be "best buds" with security researchers
MalwareHunterTeam found Exotic 1.0 on October 12, when, as he usually likes to do, he started a group analysis on Twitter to share information on the new threat with other analysts. As is sometimes customary, one of the researchers recorded a video of the ransomware in action, walking other researchers through the infection process.
To everyone's surprise, the ransomware author contacted the researcher and thanked him for the time he took to showcase his "work" and make the video, and even wanted to become friends on Skype, as these screengrabs show. This gesture took many by surprise, since malware authors usually do everything in their powers to avoid security researchers and their prying eyes, especially ransomware analysts, who many times crack encryption algorithms, ruining their operations.
Researchers found Exotic 2.0 and Exotic 3.0 during the next two days, but they both contained minimal changes. At the time of writing, there is no spam or malvertising campaign pushing this threat.
Exotic locks files and asks for only $50
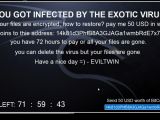
As for Exotic's technical capabilities, the ransomware works by encrypting files with the AES-128 algorithm and requiring the user to pay a ransom of $50 in Bitcoin.
At the file level, the ransomware encrypts files, gives them a random name, and replaces the original extension with ".exotic".
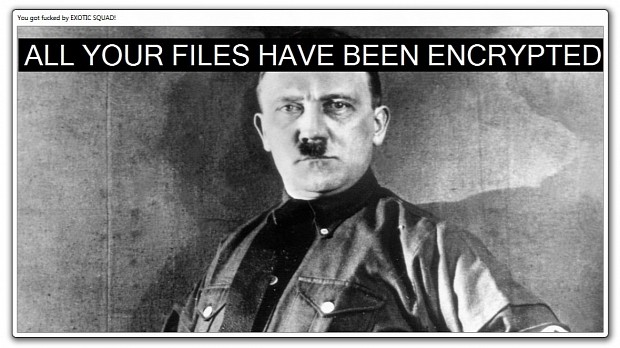
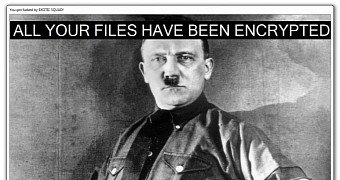
Exotic 1.0 is easy to spot because it uses an image of Hitler for the ransom note background, probably inspired by the Hitler ransomware that appeared at the start of August. The other two versions dropped this image and used a minimal lock screen inspired by the Jigsaw ransomware. This is nothing out of the ordinary, and most ransomware works following the same pattern.
The only distinctive feature about Exotic is actually a bug that initially fooled researchers into thinking it was slowing down PCs by constantly scanning computers for newly added files. In the end, it turned out that the crook targeted a few folders for encryption more than once.
The error is quite trivial, and this shows that EvilTwin has no experience working with ransomware, which most security researchers suspected since the beginning.
Below is a video from Serbian security researcher GrujaRS showing an Exotic 3.0 infection taking root and locking down a PC.
 14 DAY TRIAL //
14 DAY TRIAL //