Malware authors offering free-to-download versions of their malicious software lowers the bar and skills needed to enter the cyber-crime scene.
The freemium model has long been around in software development. Since the early days of e-commerce, software developers have figured out that by offering a free but feature-limited version of their apps, they could draw in more sales later on, as users got accustomed to their software package and wanted access to more features.
This hasn't been the case with malware, where crooks were only interested in making a quick buck, and have always been offering malware under a commercial license only.
But the freemium model is slowly making its way among malware developers, with negative consequences on the rest of us.
Meet Viotto, the cybersecurity consultant
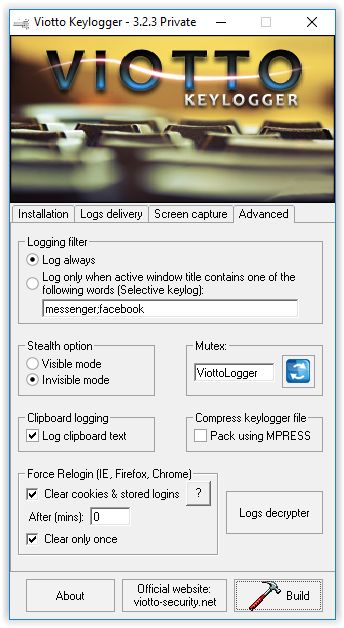
One such example is the Italian malware developer Viotto, who claims to be a "cybersecurity consultant" and "malware analyst," but is offering tools such as keyloggers, RATs, spambots, and software crypters on his website.
Viotto is also the author of a new RAT that launched over the summer called Remcos, which we covered when it came out. Viotto is offering Remcos under a dual freemium and commercial license, a distribution model he also uses for most of the malicious software on his site.
The direct consequence of this licensing scheme is the availability of free malware that anyone can deploy. Sure, you can argue that hacking forums are full of cracked versions of commercially-available tools, but there's also the danger of those cracked versions being booby-trapped to hack the hackers. In most cases, cyber-criminals will trust a malware author that offers his software for free on his own terms.
Why is this important? Because this helps unskilled crooks put together malware distribution campaigns with minimal costs, without having to spend a large amount of time working on their code or hiring professional coders.
Free version of Viotto Keylogger detected in live attacks
One such example is a recent spear-phishing campaign discovered by the team at PhishMe. Experts say that crooks were spreading a keylogger to victims, which at a later analysis proved to be the feature-limited, but still dangerous Viotto Keylogger, developed by the aforementioned "cybersecurity consultant" Viotto.
Despite being limited in features, the keylogger was more than enough to carry out cyber-espionage on infected targets. Additionally, the fact that the Viotto Keylogger was developed in 2011 also didn't stop the attackers from using it.
In the big picture, scenarios like these, where cyber-criminals deploy outdated, freely available, and generally low-level malware, are more common than you think. Despite being a laughable effort at delivering malware, it only takes one employee falling for this trick for a company to get hacked and suffer huge damages.
 14 DAY TRIAL //
14 DAY TRIAL //