- By Catalin Cimpanu
- October 18th, 2016

WordPress Sites Under Attack via Security Flaw in Unmaintained Plugin
Users advised to uninstall plugin as soon as possible
- By Catalin Cimpanu
- October 14th, 2016

Mirai IoT DDoS Trojan Now Targets Cellular Network Equipment
Mirai trojan becomes more dangerous by targeting critical equipment in mobile 3G and 4G LTE networks
- By Catalin Cimpanu
- October 6th, 2016
Beware of New Steam Spam Leading to Malware
Malware allows attackers to take over infected PCs
- By Catalin Cimpanu
- September 21st, 2016

Australian Police Warns of Dangerous USB Drives Left Inside Letterboxes
Crooks find a new way of delivering malware to their targets
- By Catalin Cimpanu
- September 20th, 2016

This Microsoft Engineer Has a Really Good Argument for Ditching SMBv1
Sysadmins should remove or disable SMBv1
- By Catalin Cimpanu
- September 15th, 2016

Hackers Actively Scanning Drupal Sites for Vulnerability Patched in July
Attackers looking for vulnerable Drupal 7.x sites
- By Catalin Cimpanu
- September 13th, 2016

Armada Collective DDoS Extortion Group Now Threatens Ransomware Infections
DDoS extortion campaigns continue even today
- By Catalin Cimpanu
- September 10th, 2016

Is Using Remote Access Trojans (RATs) to Monitor Your Kids Acceptable?
These days, parents can easily end up installing RATs instead of legitimate parental control software
- By Catalin Cimpanu
- September 9th, 2016
SNMP Port Scans Increase Following Rapid7 Vulnerability Report
High-end NMS products affected by several security issues
- By Catalin Cimpanu
- September 9th, 2016

Email Marketing Trick Incorporated in Hacking Arsenals
Pixel tracking used for mapping internal networks, detecting the efficiency of phishing and spear-phishing campaigns
- By Catalin Cimpanu
- August 29th, 2016

Tech Support Scammers Find New Trick to Hijack Chrome Browsers
Scammers put the user's browser in fullscreen mode and show a fake Google UI toolbar at the top in the form of a JPEG
- By Catalin Cimpanu
- August 19th, 2016

This Tor Error Will Likely Scare a Lot of Unsuspecting IPv6 Users
Tor should disable IPv6 for its servers until the protocol is properly supported by its software, says crypto-guru
- By Catalin Cimpanu
- August 18th, 2016

Bitcoin Website Issues "State-Sponsored Attack" Warning
Bitcoin Project issues danger-level alert
- By Catalin Cimpanu
- August 12th, 2016
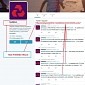
Scammers Hijack Customer Support Requests on Twitter
Clever trick sends users to dangerous phishing sites
- By Catalin Cimpanu
- August 11th, 2016
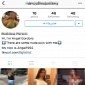
Trend of Hacked Instagram Accounts Promoting Adult Links Gets Worse and Worse
Attackers are no taking over real accounts for good
- By Catalin Cimpanu
- August 10th, 2016
Chrome, Firefox, and IE Browser Hijacker Distributed via Legitimate Software
Intel McAfee warns users about Lavians software
- By Catalin Cimpanu
- August 10th, 2016

Powerful Android Adware Makes Its Way Into the Google Play Store
Apps are still available for download at the time of writing





