Crooks are using look-alike Twitter accounts to insert themselves into legitimate customer support Twitter conversations and lead customers back to phishing sites to collect their login credentials and account details.
Even if this clever scam is two years old, it continues to make victims even today, as a security researcher going by the name of Techhelplist discovered two days ago.
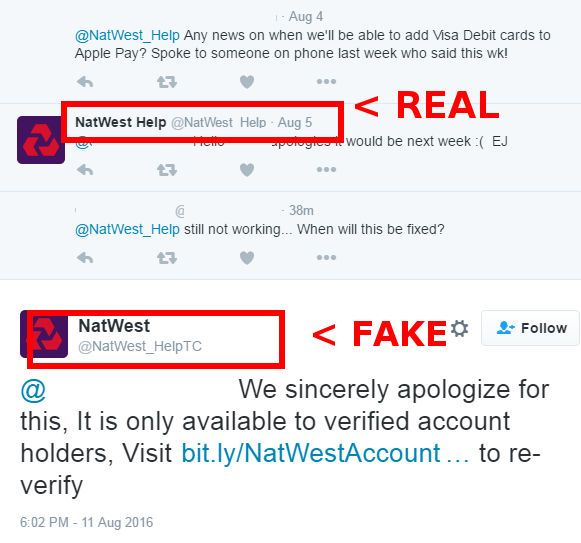
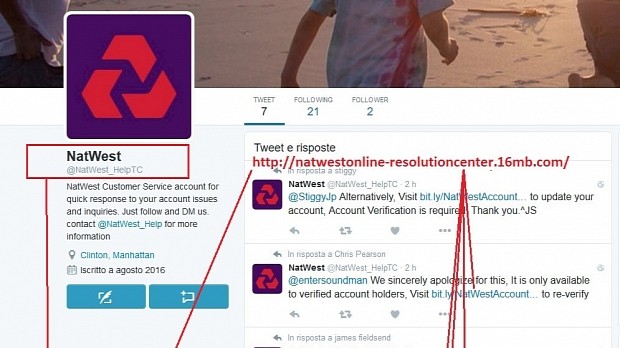
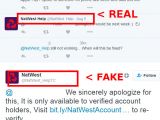
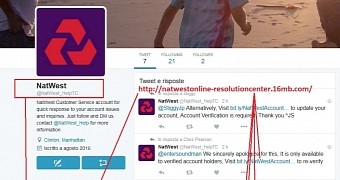
In this latest case, scammers targeted the Twitter account of NatWest (National Westminster Bank). The official account is @NatWest_Help, but crooks created the @NatWest_HelpTC in order to fool users.
Scammers attack when customer support staffers are off duty
Whenever the official customer support account went dormant, the crooks would take it as a sign that the PR or customer support staff was off duty. They would then swoop in and reply to Twitter conversations where users were asking for help.
Most times, the scammers would trick users by saying that a particular feature was only available for verified accounts and requesting the user to verify their account. Conveniently, the crooks would also tweet a link where the user could do so.
In most cases, the link would be shortened via services like Bit.ly so that the user wouldn't be able to see its real URL, which in all instances had nothing to do with the bank's online portal.
Customers looking for legitimate help would be sent to a phishing page that was logging their credentials and any other details the crooks would be asking. If their phishing page were to be taken down, then they'd just create another one and spread that one instead.
Keep these tips in mind
"This was a particularly clever scamming technique back in 2014, and it remains as slick as ever in 2016," Christopher Boyd writes for Malwarebytes, also offering the following tips:
“ Most - if not all - financial services offering support on Twitter will have a blue Verified tick. Please note that many non-financial areas of business on twitter don’t always possess a tick, and this shouldn’t be used as conclusive proof one way or the other. ”
“ Is the support account trying to send you to a website? Is your query, which doesn’t really require a website visit, being immediately directed to somewhere you have to login? Is the website asking you to login sitting on a free webhost / not a HTTPS site? If so, you should probably steer clear. ”
“ Does the support account have very few followers? If the brand is an established one, it’s probable that they have a lot more than 2, like the scam account up above. ”
“ Pay close attention to any and all replies – 10 seconds spent ensuring the Twitter URL of the account messaging you matches the account you initially spoke to is infinitely preferable to losing your bank login to a scammer. ”
 14 DAY TRIAL //
14 DAY TRIAL //