- Security
- By Eduard Kovacs
- December 30th, 2013

RFID-Based Master Key Cards Can Be Hacked, Experts Warn
It's not that difficult to open the door to your apartment building
- Security
- By Eduard Kovacs
- December 30th, 2013

Vulnerabilities in SD Cards Can Be Exploited for MITM Attacks
Researchers have presented their findings at 30C3
- Security Blog
- By Eduard Kovacs
- December 28th, 2013

Researchers Find Critical Vulnerability in Samsung Knox
The flaw can be leveraged to bypass the protection provided by the secure container
- Security Blog
- By Eduard Kovacs
- December 27th, 2013
FeedBurner.com Page Set Up to Serve JavaScript Trojan
Cybercriminals are abusing the Google feed management service
- Server related
- By Eduard Kovacs
- December 27th, 2013
Cybercriminals Abuse Network Time Protocol for DDOS Attacks
Symantec researchers have spotted an increase in the number of such attacks
- Security Blog
- By Eduard Kovacs
- December 27th, 2013

Possible Owner of Service Selling Target Payment Card Data Identified
He appears to be a Ukrainian named Andrey Hodirevski
- Virus alerts
- By Eduard Kovacs
- December 27th, 2013
Syrian Government Supporters Target Journalists, NGOs and Opposition with Malware
A new research paper published by the EFF and Citizen Lab
- Virus alerts
- By Eduard Kovacs
- December 20th, 2013

CryptoLocker 2.0 Appears to Be the Work of Copycats
ESET researchers have analyzed the new file-encrypting malware
- Security Blog
- By Eduard Kovacs
- December 19th, 2013
Trojan.Ferret: New DDOS Malware Likely Developed by Russians
Arbor Networks researchers have analyzed the threat
- Security Fixes and Improvements
- By Eduard Kovacs
- December 19th, 2013

Full 4096-Bit RSA Keys Extracted by Listening to the Sound Made by Computers
Experts have tested their attack against GNU Privacy Guard
- Virus alerts
- By Eduard Kovacs
- December 19th, 2013

ZeuS Trojan Variant Targets Accounts of BTC China Customers
Trusteer researchers have analyzed the Gameover malware
- Virus alerts
- By Eduard Kovacs
- December 18th, 2013
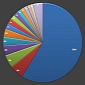
Experts Analyzed DGA.Changer Malware Served in PHP.net Attack
Seculert says the threat is mainly designed to download other pieces of malware
- Security Blog
- By Eduard Kovacs
- December 18th, 2013
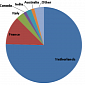
Qadars Banking Trojan Targets Users from the Netherlands
The threat uses web injects and Android modules to steal sensitive information
- Virus alerts
- By Eduard Kovacs
- December 18th, 2013
ChewBacca: Infostealer Malware Uses Tor for C&C Infrastructure
Kaspersky researchers say the Trojan is not sold publicly
- Virus alerts
- By Eduard Kovacs
- December 18th, 2013
Skimmer Trojan Targets ATMs Made by One of the World’s Largest Manufacturers
Doctor Web researchers have analyzed the new threat
- Virus alerts
- By Eduard Kovacs
- December 18th, 2013

CERT Poland Warns of DDOS Botnet Targeting Windows and Linux Machines
Linux machines are likely targeted because they're usually servers with a lot of bandwidth
- Virus alerts
- By Eduard Kovacs
- December 17th, 2013
Browlock Cybercriminals Use Malvertising to Lure Victims to Malicious Site
Symantec has blocked 650,000 connections in November