Security researchers from Symantec say the Browlock ransomware leverages malvertising in order to attract users to a malicious website.
Earlier this year, researchers uncovered an interesting piece of browser-based ransomware. The threat, dubbed Browlock, doesn’t encrypt files and it doesn’t lock computers’ screens. Instead, it simply displays a warning message in the browser and uses JavaScript to prevent victims from closing the window.
Symantec experts have been monitoring Browlock and they’ve found that a lot of users have been targeted. In November, for instance, Symantec’s products blocked over 650,000 connections to the malicious website used by Browlock.
It’s worth noting that these were only the attacks aimed at Symantec customers. The actual number of connections is probably much higher.
So how do users end up on the malicious website? Researchers say the cybercriminals are using malvertising. They’ve purchased traffic from companies specializing in adult advertising.
When users click on an ad, they’re taken to what appears to be an adult website, after which they’re redirected to the Browlock site.
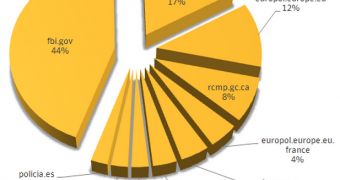
On this site, victims are presented with a warning message and a URL that matches their location. For example, internauts from the US will be served a URL that looks something like “fbi.gov.a5695.com” and the warning message will appear to be from the FBI.
The names of law enforcement agencies from 25 regions are leveraged in these attacks, including Europol and police from Sweden, Spain, Germany, France, Australia, Italy and the Netherlands.
Experts believe that the tactics used by the cybercriminals behind Browlock are very efficient because they don’t have to pay for a malicious executable or for an exploit kit to deliver the payload. On the other hand, they need to spend some money on the traffic that drives potential victims to the malicious website.
 14 DAY TRIAL //
14 DAY TRIAL //