- Security Blog
- By Ionut Ilascu
- November 4th, 2014
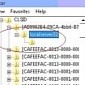
Fileless Poweliks Malware Distributed Through Spam and Exploit Kits
Although different, malware uses regular distribution method
- Security
- By Ionut Ilascu
- September 3rd, 2014
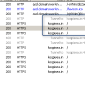
Stealthy Malware Leaves No File on the System
Persistence is not achieved, but it may be by design