- Security Blog
- By Eduard Kovacs
- October 5th, 2012
“Is This Your Skype Profile Pic?” Spam Uses Short Google URLs to Spread Trojan
Victims become entangled in a network of compromised machines
- Security
- By Bogdan Popa
- October 4th, 2012

FTC Shuts Down International Phone Scam Network
Consumers were tricked into paying for non-existent virus infections
- Software Blog
- By Bogdan Popa
- October 3rd, 2012

Canada Leads the Anti-Malware Global Effort – Microsoft
New data shows that Canadians are much more secure than other users
- Security Blog
- By Eduard Kovacs
- October 2nd, 2012
![Crocodile Hunter Teaches You How to Stay Protected Online [Video Parody] Crocodile Hunter Teaches You How to Stay Protected Online [Video Parody]](https://news-cdn.softpedia.com/images/news2/Crocodile-Hunter-Teaches-You-How-to-Stay-Protected-Online-Video-Parody-1.png)
Crocodile Hunter Teaches You How to Stay Protected Online [Video Parody]
A highly amusing advisory presented by StopBadware.org and Bluehost
- Security Blog
- By Eduard Kovacs
- October 1st, 2012

Quervar Malware Found to Download ZeroAcess Trojans and Ransomware
The new variant was identified on September 27 by Trend Micro
- Security Blog
- By Eduard Kovacs
- September 28th, 2012
Fake AV “System Progressive Protection” Distributed via Drive-By Downloads
The malware prevents users from accessing the apps on their computers
- Security Blog
- By Eduard Kovacs
- September 27th, 2012

Dorifel Infected over 30 Government and Private Organizations in the Netherlands
The indirect damages caused by the malware are 10,000 - 50,000 EUR ($13,000 – $64,000)
- Security Blog
- By Eduard Kovacs
- September 26th, 2012

Best Themes Songs for Hacking, DDOS Attacks and Malware Payloads
“Seek and Destroy” by Metallica is appropriate when destroying data, because Metallica is appropriate for everything
- Security
- By Eduard Kovacs
- September 25th, 2012

Security App of the Week: Block LinkBucks
A browser extension designed to bypass annoying or malicious advertisements
- Security Blog
- By Eduard Kovacs
- September 25th, 2012
Imuler.B Mac Malware Designed to Avoid Wireshark, Experts Say
The new version of the Mac OS X threat comes with some improvements
- Security Blog
- By Eduard Kovacs
- September 25th, 2012

KLM e-Ticket Notification Comes with Malicious Attachment
A piece of malware allows cybercriminals to remotely access the victims' computers
- Security Blog
- By Eduard Kovacs
- September 24th, 2012
“Your in This” Twitter Spam Leads to Malicious Facebook Video
A rogue Flash Player update is advertised via direct messages
- Spam Reports
- By Eduard Kovacs
- September 21st, 2012
Amazon “Amazin’ HD TV” Purchase Emails Lead to Trojan
Users are tricked into visiting a website that's designed to serve malware
- Security Blog
- By Eduard Kovacs
- September 20th, 2012
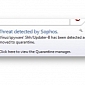
Sophos Antivirus Detects Its Own Components as Malware
In some cases, a file needed to perform updates has been deleted
- Virus alerts
- By Eduard Kovacs
- September 20th, 2012

“Twitter Video” Facebook App Spreads via DMs, Leads to Malware
Victims are lead to believe that a fail video of them is making the rounds online
- Security
- By Bogdan Popa
- September 20th, 2012

Security Vulnerability in Windows 8 Can Lead to Malware Infection
Rootkit-based malware could be installed on a Windows 8 machine
- Virus alerts
- By Eduard Kovacs
- September 20th, 2012
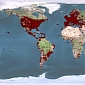
Over 1 Million PCs Currently Part of ZeroAccess Global Botnet
The threat is helping cybercriminals earn as much as $100,000 (80,000 EUR) per day