- Security
- By Eduard Kovacs
- June 27th, 2013

FireEye Helps IT Security Pros Identify the Origin of Advanced Cyberattacks
The company has also identified a new attack tactic used by the Comment Crew
- Security Blog
- By Eduard Kovacs
- June 27th, 2013
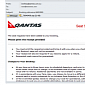
Gamarue Malware-Spreading Emails Purporting to Come from Qantas Spotted Again
Trustwave’s SpiderLabs has analyzed the malicious messages
- Virus alerts
- By Eduard Kovacs
- June 27th, 2013

Link Found Between March and June Attacks Against South Korea
A time-triggered piece of malware is responsible for the DDOS attacks
- Virus alerts
- By Eduard Kovacs
- June 26th, 2013

Fake Xbox One Emulator Advertised on YouTube Hides Malware
Malwarebytes experts have analyzed the Xbox One scam
- Security Blog
- By Eduard Kovacs
- June 26th, 2013
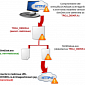
SimDisk Auto-Update Mechanisms Compromised, Abused Against South Korean Users
Cybercriminals altered the installer to distribute a malicious file
- Virus alerts
- By Eduard Kovacs
- June 26th, 2013
Carberp Malware Source Code Leaked
Researchers are still analyzing the code, but they've confirmed that it's genuine
- Web Blog
- By Lucian Parfeni
- June 25th, 2013
Google Adds Malware Data from All Over the World to Its Transparency Report
Google has a great overview of the web, including the seedier parts
- Virus alerts
- By Eduard Kovacs
- June 25th, 2013
Chinese Hackers Use PinkStats Malware Against South Korean Organizations
The malware has been used in cyberattacks since 2009
- Security
- By Eduard Kovacs
- June 25th, 2013
Only 6% of Companies Recognize the True Scale of Malicious Software, Study Shows
2013 Global Corporate IT Security Risks report by Kaspersky and B2B International
- Virus alerts
- By Eduard Kovacs
- June 22nd, 2013
DirtJumper Malware Version Dubbed “Drive” Sports Powerful DDOS Engine
Arbor Networks researchers have analyzed the new variant
- Security Blog
- By Eduard Kovacs
- June 21st, 2013

Information-Stealing Fareit Malware Used Against Wells Fargo Customers
The Trojan is capable of performing a wide range of malicious activities
- Web Blog
- By Lucian Parfeni
- June 20th, 2013

The Chrome Web Store Gets Improved Spam and Malware Check
Google is warning developers that it may take longer for apps to go live
- Security Blog
- By Eduard Kovacs
- June 19th, 2013
Malware Alert: “Hey User Your Facebook Account Has Been Closed!”
Avast! experts provide a detailed technical analysis of the attack
- Security Blog
- By Eduard Kovacs
- June 19th, 2013
Government Security News and 60 Other Websites Hacked, Abused to Serve Malware
Java vulnerabilities exploited to push the ZeroAccess Trojan
- Security Blog
- By Eduard Kovacs
- June 15th, 2013
Trojan Uses Fake Adobe Certificate to Evade Detection
Symantec experts have analyzed an interesting variant of Backdoor.Trojan
- Virus alerts
- By Eduard Kovacs
- June 14th, 2013

ZeuS Malware Used to Lure Victims to Money Mule Recruitment Website
The malware uses Man-in-the-Browser (MitB) techniques to inject ads
- Security Blog
- By Eduard Kovacs
- June 13th, 2013
Kilim Trojan Hijacks Social Media Accounts with Rogue Browser Extensions
Microsoft experts warn that social bots are on the rise