On June 25, we learned that several South Korean government websites were disrupted by distributed denial-of-service attacks. As it turns out, this latest series of attacks is somewhat similar to the operation that disrupted several broadcasters and financial institutions back in March.
According to Trend Micro, the piece of malware utilized by the cybercriminals in March was programmed to wipe the master boot record (MBR) of infected computers on March 20, 2013.
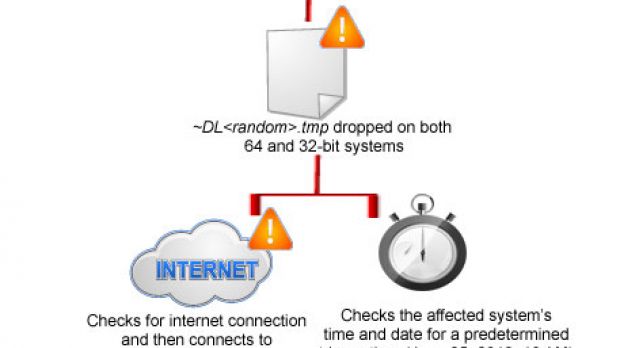
In the more recent attacks, a similar time-triggered malware, distributed via the compromised SimDisk auto-update mechanism, has been utilized. However, this time, instead of wiping the MBR, the malware was designed to drop a DDOS-capable component onto infected systems on June 25, after 10 AM.
The DDOS component is designed to send relatively large DNS packets to two IP addresses.
Since these IP addresses are associated with the primary and secondary DNS name servers used by a number of South Korean government sites, the attackers were able to disrupt several domains by targeting a single point of failure.
“The attack is intended to knock all of these sites offline indirectly: users that don’t have a DNS record cached for these domains would need to use DNS to translate the domain name to the IP address, but because the name servers for these domains are offline, they would be unable to do so,” Trend Micro experts noted.
Researchers from South Korean security firm AhnLab have also published a detailed analysis (written in Korean) of the malware used for this DDOS attack.
According to their research, the malware changes the desktop background of the infected computer with an image promoting the Anonymous movement.
In the March attacks, a message from a hacker team called the “Whois Team” appeared on the infected devices. On this occasion, the name of Anonymous was leveraged.
South Korean officials have not pointed the finger at anyone for the attacks, but it’s likely that, sooner or later, North Korea will be named as being the culprit, just like after the March attacks.
 14 DAY TRIAL //
14 DAY TRIAL //