- Virus alerts
- By Catalin Cimpanu
- August 26th, 2016

Agent Tesla Spyware Detected in Live Attacks
Agent Tesla available for sale on the public Internet
- Security
- By Catalin Cimpanu
- July 26th, 2016

KeySniffer Flaw Lets Attackers Log and Inject Keystrokes on Wireless Keyboards
The security flaw is technically unpatchable
- Security
- By Catalin Cimpanu
- July 15th, 2016

KeyBase Keylogger Shuts Down, Author Says He'll Help Police Investigations
Crooks still using the keylogger in their campaigns
- Virus alerts
- By Catalin Cimpanu
- July 4th, 2016
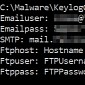
HawkEye Keylogger Users Employ Hacked Emails Accounts to Receive Stolen Data
They also leverage RTF exploits to infect users
- Security
- By Catalin Cimpanu
- May 24th, 2016

FBI Warns Against Wireless Keystroke Loggers Disguised as USB Chargers
Alert is for companies that use wireless Microsoft keyboards
- Spyware Threats
- By Catalin Cimpanu
- May 6th, 2016

Windows Trojan Logs Your Keystrokes, Takes Snapshot of Your Desktop
Trojan spread using email spam, leveraging Excel macros
- Virus alerts
- By Catalin Cimpanu
- April 20th, 2016

New PWOBot Python Malware Can Log Keystrokes, Mine for Bitcoin
PWOBot only targeted European organizations
- Incidents
- By Catalin Cimpanu
- March 28th, 2016

Hardware-Based Keyloggers Found in the Library of a Canadian University
Concordia University in Montreal, Canada, affected
- Spyware Threats
- By Catalin Cimpanu
- March 18th, 2016

Olympic Vision Keylogger Spread via BEC Scams in 18 Countries
Olympic Vision is an advanced threat that can steal key strokes, clipboard data, and user credentials
- Spyware Threats
- By Catalin Cimpanu
- February 25th, 2016
KeyBase Keylogger Usage Explodes After Getting Leaked Online
Researchers detect over 44,200 KeyBase sessions
- Security
- By Catalin Cimpanu
- February 16th, 2016

Attackers Hide Malware as Magento Security Patch to Hijack Online Stores UPDATED
Magento store owners should take great care when updating
- Spyware Threats
- By Catalin Cimpanu
- February 9th, 2016

Tool for Hacking Facebook Accounts Contains Remtasu Spyware
You should be safe if you're not trying to hack into someone else's Facebook account (using the Hack Facebook app)
- Security
- By Catalin Cimpanu
- January 11th, 2016

Smartwatches Can Be Used to Spy on Your Card's PIN Code
Wearable devices can be used as motion-based keyloggers
- Spyware Threats
- By Catalin Cimpanu
- January 10th, 2016

Spymel Info-Stealing Trojan Evades Antivirus Detection via Stolen Certificates
Zscaler researchers discover yet another malware family hiding with the help of stolen digital certificates
- Security
- By Catalin Cimpanu
- September 13th, 2015

Creepy Smartwatch Spies What You Type on a Keyboard
Researchers create a smartwatch app that can detect what you've typed based on the movements of your left hand
- Security
- By Ionut Ilascu
- June 8th, 2015
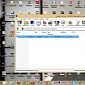
Insecure Command and Control Server Exposes Crook Testing Keylogger
KeyBase is not sophisticated but gains increased popularity
- Security
- By Ionut Ilascu
- May 29th, 2015
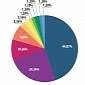
Non-Sophisticated Malware Steals Thousands of Credentials from Targeted SMBs
DarkComet RAT used to control infected computers