- Security Blog
- By Catalin Cimpanu
- May 22nd, 2016

Nine Days Later, Flash Zero-Day CVE-2016-4117 Already Added to Exploit Kits
CVE-2016-4117 spotted in Magnitude exploit kit attacks
- Security
- By Catalin Cimpanu
- May 17th, 2016

Nuclear EK Authors Are Based in Russia, Make $100,000 per Month
Crooks infected nearly 2 million computers
- Security
- By Catalin Cimpanu
- April 25th, 2016

Flash Accounted for All Top 10 Vulnerabilities Used by Exploit Kits in 2015
Java vulnerabilities were ignored almost entirely
- Virus alerts
- By Catalin Cimpanu
- April 20th, 2016
Meet Panda Banker, One of the Most Recent Zeus Banking Trojan's Offspring
Panda Banker targets only banks in Australia, the UK
- Security
- By Catalin Cimpanu
- March 30th, 2016
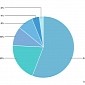
Angler Accounted for More than Half of Active Exploit Kit Installs in Q4 2015
Malicious domains near record-level numbers
- Security
- By Catalin Cimpanu
- March 1st, 2016

Constant Updates Keep Angler EK More Efficient than Ever
Angler adds new tricks to stay ahead of security researchers
- Security
- By Catalin Cimpanu
- February 20th, 2016

TeslaCrypt Ransomware Campaign Extends from WordPress to Joomla Sites
Crooks expand the scope of their operation to include Joomla
- Security
- By Catalin Cimpanu
- February 10th, 2016
Malware Distributors Use Fake CloudFlare DDoS Checks to Trick Users
Fake DDoS protection system actually sends users to an EK
- Security Blog
- By Catalin Cimpanu
- February 5th, 2016

Campaign of Compromised WordPress Websites Now Spreading Ransomware
Campaign operators switch from pushing the Backdoor.Andromeda malware to the TeslaCrypt ransomware instead
- Security
- By Catalin Cimpanu
- January 18th, 2016

The Number of Flash Vulnerabilities Tripled in 2015
Over ten crypto-ransomware families detected in 2015
- Security
- By Catalin Cimpanu
- January 12th, 2016

Exploit Kit Usage Explodes at the Start of 2016
Cyber-security vendors report on an increase in exploit kits
- Security
- By Catalin Cimpanu
- December 16th, 2015
Comcast Users Hit by Malvertising, Exploit Kit, Tech Support Scam in One Go
Trio of threats assaults unsuspecting Comcast Xfinity users
- Security
- By Catalin Cimpanu
- December 6th, 2015

Infostealers, Exploit Kits & Ransomware, Just Your Typical Malware Campaign
A look inside your typical malware campaign
- Security
- By Catalin Cimpanu
- November 28th, 2015
CryptoWall 4.0 Ransomware Already Part of Exploit Kits
Campaign was active even before we knew about CryptoWall 4.0
- Security
- By Catalin Cimpanu
- November 19th, 2015
Blackhole Exploit Kit Resurfaces 2 Years After Its Author Went to Jail
Blackhole exploit kit spotted in attacks over the weekend
- Security
- By Catalin Cimpanu
- November 18th, 2015
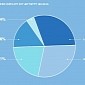
Exploit Kit Activity Goes Up 75 Percent
Angler, Magnitude, Neutrino & Nuclear, the most popular EKs
- Security
- By Catalin Cimpanu
- November 9th, 2015

Adobe Flash Accounts for 8 of the Top 10 Vulnerabilities Used in Exploit Kits
Internet Explorer and Silverlight get the other 2 spots