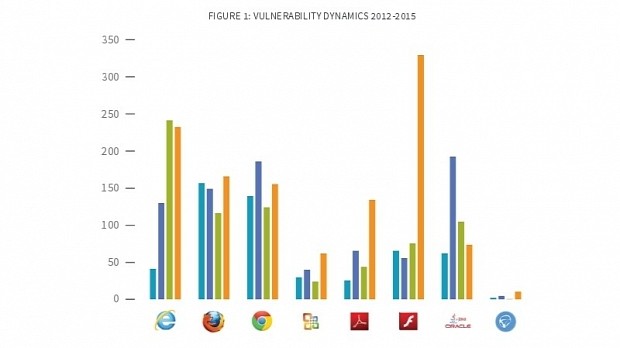
A new report by Bromium comes to confirm that 2015 was a terrible year for Flash, which saw a spike in the number of new vulnerabilities detected but also in off-the-shelf ready-available exploits.
According to Bromium, security researchers saw an increase of 60% in the number of newly discovered application vulnerabilities when compared to 2014.
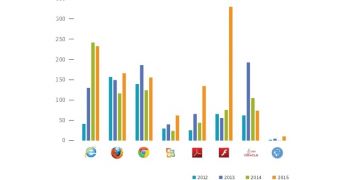
Flash is the biggest offender, once again
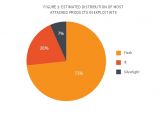
The biggest riser was Flash, which increased 333%, mainly due to the Hacking Team data breach that exposed many zero-day bugs, all at the same time.
Additionally, Flash also saw a 200% increase in the number of off-the-shelf exploits added to the Metasploit pen-testing / hacking framework, a toolkit often used by security researchers and malware builders alike.
"The architecture of Adobe’s AVM has multiple flaws allowing attackers to craft reliable exploitation techniques like ROP shellcode on the fly, thus bypassing ASLR, DEP and other protections," Bromium researchers explain.
Furthermore, Flash was also the favorite tool for exploit kit builders, which deployed Flash exploits via their infection tools in 73% of the cases.
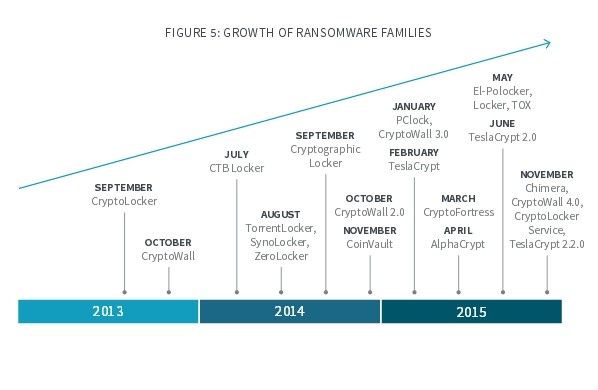
2015 was the year of the ransomware
As for IE, another tool favored by hackers, Bromium says that Internet Explorer saw a drop-off that can be explained by Microsoft's efforts to add security measures such as isolated heap, Control Flow Guard, and sandboxing.
But the security landscape is not comprised by Flash security flaws alone. According to Bromium, 2015 also saw an increase in macro-malware, email spam, and especially crypto-ransomware.
Bromium estimates that, in 2015, 10 crypto-ransomware families were active at one point or another, with Cryptowall and TeslaCrypt being the most active. Overall, the number of ransomware strains grew 600% when compared to 2014.
Most of it, as Bromium explains, was distributed via macro-malware and email spam, and the researchers also noted the rise of Ransomware-as-a-Service operations like TOX and Crypto Locker Service (CLS).
The Bromium Endpoint Exploitation Trends 2015 report is available for download.
 14 DAY TRIAL //
14 DAY TRIAL //