- Security
- By Ionut Ilascu
- March 9th, 2015

BandarChor Ransomware Infections Increase
Threat is atypical, victims asked to send email to crooks
- Security
- By Ionut Ilascu
- February 20th, 2015

TrueCrypt Audit Part Two Is on Its Way
Researchers used their spare time to work on the project
- Security
- By Ionut Ilascu
- February 6th, 2015

French Businesses Under Ransomware Fire
Large bill for electronic products is used as a lure
- Security
- By Ionut Ilascu
- January 12th, 2015
TorrentLocker Operators Make $224,000 in About a Month
Most of the money comes from victims in Australia
- Virus alerts
- By Ionut Ilascu
- December 17th, 2014
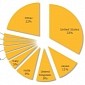
CryptoLocker Variant Has Been Created Specifically to Target Japanese Users
Compromised websites is the main distribution method
- Editorials
- By Ionut Ilascu
- December 14th, 2014
2015 Could Be the Year of the Ransomware
Small and mid-sized businesses may be hit more often
- Security
- By Ionut Ilascu
- November 3rd, 2014

TextSecure Is a Safe Chat Client, Researchers Find
Eliminating the risk of unknown key-share attack is possible
- Security
- By Ionut Ilascu
- October 24th, 2014
Adobe Digital Editions Now Encrypts Data Collected from Users
Sending information about user activity is never a good idea
- Virus alerts
- By Ionut Ilascu
- October 23rd, 2014

CryptoWall 2.0 Rampage: 84 New Variants Spotted in Less than a Month
New version seems to be popular among cybercriminals
- Security
- By Ionut Ilascu
- October 22nd, 2014

TorrentLocker Ransomware Reaches Italy and Brazil, Affects Thousands
Ransom asked to be paid in digital currency Bitcoin
- Security
- By Ionut Ilascu
- October 20th, 2014

Android Malware Can Be Delivered Stealthily as an Image or a PDF File
Researchers create technique that allows control over the input and the output of AES CBC encryption process
- Security
- By Ionut Ilascu
- August 27th, 2014

Crypto-Malware Steals Email Addresses and Passwords, Spreads Itself
Malicious tool relies on free software to carry out nefarious tasks
- Security
- By Ionut Ilascu
- August 11th, 2014

Yahoo Ad Network Used to Spread CryptoWall Ransomware
Major ad networks are targeted by cybercriminals all the time
- Security
- By Ionut Ilascu
- August 11th, 2014

Blackphone Vulnerability Soon to Receive Full Fix
Developer collaborating with the hacker to release a patch
- Security
- By Ionut Ilascu
- August 2nd, 2014

Simple Ransomware Relies on GnuPG for Encryption
Main module is a batch file that executes the commands
- Security Blog
- By Ionut Ilascu
- July 15th, 2014

Tutanota Spy-Proof Email Service Patched Against XSS Risk
Developers announce improved security for the future release
- Security
- By Ionut Ilascu
- July 4th, 2014

Cryptocat Developer to Deliver Simple Tool for Complex Encryption
Browser extension eliminates private key management