An increase in the number of infections caused by the BandarChor ransomware with file encryption capabilities has been observed by security researchers.
The malware usually arrives on the victim’s computer via a malicious email, but there is indication that it may also be included in certain exploit kits.
Backup files also included for encryption
F-Secure noticed the first computers infected with this relatively new family of ransomware in November 2014, but the encounters have decreased since then.
Over the past week, new reports have popped up pointing to systems affected with BandarChor.
Researchers say that immediately after compromising the machine the malware copies itself into the Startup folder, where it also places the ransom message under the form of an image file.
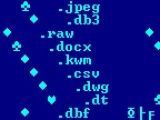
During the encryption process, the malware tries to lock document and image files, as well as other data, with the following extensions: DOC, XLS, JPG, ZIP, CDR, MKV, TXT, RTF, PDF, ODT, M2V, MOV, DWG, CSV, DOCX, PPT, AVI, MDB and TIB (used by Acronis for storing backup files).
By analyzing BandarChor’s behavior, researchers noticed that the name of the encrypted files was changed, adding the “.id-[ID][email protected]” suffix.
Operators use unusual method to get paid
As soon as the data becomes hostage, it communicates the computer name and the ID to a remote command and control server via a HTTP POST request.
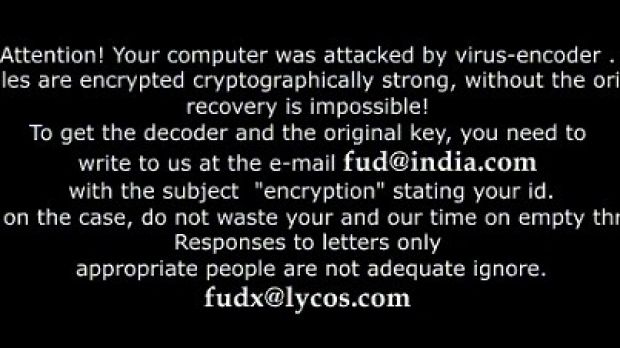
The ransom message is simple and states that the computer of the victim has been “attacked by virus-encoder” and that the encryption method used is a strong one, not allowing a reverse procedure without the original key.
In order to retrieve the decryption key, users are instructed to send a message to an email address, with the subject “encryption” and the ID assigned by the malware.
This definitely does not follow the pattern of infamous ransomware currently circulating in the wild, whose operators do not risk exposure by providing anything else than the bitcoin wallet address where the ransom fee should be directed.
F-Secure provides a list of domains that have been associated with BandarChor, as well as a list of hashes for the malware.
 14 DAY TRIAL //
14 DAY TRIAL //