- Security
- By Gabriela Vatu
- June 5th, 2014

Skype Users Face Security Risk Due to Unencrypted Data
The database can reveal the users' conversations, personal information and more
- Internet Life
- By Gabriela Vatu
- April 29th, 2014

How to Protect Yourself from Internet Explorer Vulnerability
There are ways to make sure you're not going to fall prey to hackers
- Security
- By Eduard Kovacs
- January 15th, 2014

Amazon, Google and GoDaddy Cloud Services Increasingly Abused by Cybercriminals
Solutionary has released its threat report for the fourth quarter of 2013
- Security
- By Eduard Kovacs
- October 31st, 2013

Cybercriminals and NSA Spying Cause 350% Increase in Tor Traffic
Solutionary has released its Threat Intel report for Q3 2013
- Security
- By Eduard Kovacs
- October 24th, 2013

Solutionary Enhances Its ActiveGuard Security and Compliance Platform
Check out the improvements made to the company's managed security services offering
- Security
- By Eduard Kovacs
- July 23rd, 2013

Q2 Report from Solutionary Analyzes OpUSA, PRISM and DNS Amplification Attacks
73% of websites compromised in OpUSA were hosted on IIS Web servers
- Security
- By Eduard Kovacs
- June 17th, 2013

Nippon Telegraph and Telephone Corp to Acquire Solutionary
The deal will be closed in the third quarter of this year
- Hacking News
- By Eduard Kovacs
- April 26th, 2013
North Korea's Political Environment Appears to Influence Cyberattacks, Experts Find
Solutionary has found an interesting connection between attacks and political decisions
- Security
- By Eduard Kovacs
- April 4th, 2013

Post-Attack Tasks Are Just as Important as Mitigating an Active Attack, Experts Say
Solutionary Director of Research Robert Kraus shares some insight
- Security Fixes and Improvements
- By Eduard Kovacs
- March 23rd, 2013
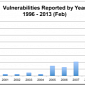
Evolution of Java Security Vulnerabilities from 1996 to 2013
Solutionary experts share some insight on Oracle's attempts to make Java more secure
- Security
- By Eduard Kovacs
- March 12th, 2013

Most Attacks Against US Companies Originate from US-Based Sources, Study Finds
Solutionary has released its Global Threat Intelligence Report
- Security Blog
- By Eduard Kovacs
- February 6th, 2013

Security Framework Recommendations from Solutionary
Some valuable advice for organizations on how to lay out a plan
- Advisories
- By Eduard Kovacs
- January 30th, 2013

Incident Response Is Only the First Step in Proactive Threat Mitigation, Experts Say
Solutionary has published an interesting advisory
- Security
- By Eduard Kovacs
- January 23rd, 2013

Solutionary Q4 2012 Report: 70% of Exploit Kits Originated in Russia
The security firm has released its Q4 Threat Report
- Security Blog
- By Eduard Kovacs
- December 19th, 2012

All Businesses That Process, Store or Transmit Payment Card Data Must Be PCI Compliant
Experts from security firm Solutionary explain what merchants should do
- Security
- By Eduard Kovacs
- December 14th, 2012

Most Organizations Find Threat Intelligence Reports Highly Useful, Study Finds
83% use them to shape their security strategies
- Advisories
- By Eduard Kovacs
- December 14th, 2012

Recent DDOS Attacks Have Made Organizations Increase Mitigation Controls, Expert Says
Rob Kraus, director of Solutionary’s Security Engineering Research Team, offers insight