- Security
- By Eduard Kovacs
- August 29th, 2013
Cybercriminals Use Aggressive Social Engineering Tactics Against French Organizations
Symantec continues to monitor the campaign dubbed "Operation Francophoned"
- Security Blog
- By Eduard Kovacs
- August 15th, 2013
Frutas RAT Used in Targeted Attacks Against High-Profile Companies in Asia and Europe
Symantec researchers say the RAT is used to gather intel for future attacks
- Security Blog
- By Eduard Kovacs
- July 17th, 2013

Cybercriminals Launch Tool to Repackage Legitimate Android Apps with RAT
Symantec has already spotted 23 legitimate apps trojanized with AndroRAT
- Security Blog
- By Eduard Kovacs
- July 6th, 2013
Java RAT Used in Spear Phishing Attacks Against US Government Agencies
Because the RAT is a Java applet, it can run on several operating systems
- Security Blog
- By Eduard Kovacs
- July 3rd, 2013
Government, Telecom and Energy Sectors in the Middle East Targeted with njRAT
Fidelis Security Systems researchers have analyzed the threat
- Security Blog
- By Eduard Kovacs
- June 24th, 2013

Ghost RAT Distributed via Taiwan Bureau of National Health Insurance Phishing Emails
One individual suspected of being involved in the scheme has been arrested
- Security Blog
- By Eduard Kovacs
- June 21st, 2013

PoisonIvy Variant Abuses Legitimate Application as Loader
The technique is called binary planting, or DLL preloading attack
- Virus alerts
- By Eduard Kovacs
- June 14th, 2013
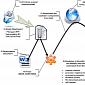
RARSTONE RAT Used in Targeted Attacks Against Asian Organizations
Trend Micro experts have analyzed the campaign they call Naikon
- Security Blog
- By Eduard Kovacs
- May 7th, 2013
AutoIt Scripting Language Increasingly Used by Malware Authors
Trend Micro experts have identified numerous malicious tools
- Green
- By Laura Sinpetru
- March 21st, 2013

Rat Reportedly Caused Fukushima's Power Failure
The rodent chewed on some cables, caused a short circuit
- Oddiverse
- By Raluca Anghel
- March 8th, 2013

Foot-Long (30-Cm) Rat Attacks Sleeping Girl, Is Killed by Dog
Francesca Williams' face and arm were bitten by the large rodent
- Security Blog
- By Eduard Kovacs
- March 5th, 2013

New RemoteIt RAT Advertised on Hacker Forums
Security researcher Suriya Prakash has analyzed the RAT
- Virus alerts
- By Eduard Kovacs
- February 28th, 2013

Cybercriminals Rely on Legitimate NVIDIA App in Attacks Against Tibetans
The attackers' goal is to drop a version of the PlugX RAT onto the target host
- Virus alerts
- By Eduard Kovacs
- February 28th, 2013

Trend Micro Warns of New BKDR_RARSTONE Remote Access Trojan
The RAT uses some clever techniques to take control of a machine
- Security Blog
- By Eduard Kovacs
- February 12th, 2013

Frutas: Java-Based Cross-Platform RAT
Symantec experts have analyzed the tool that is mainly used by Spanish hackers
- Virus alerts
- By Eduard Kovacs
- January 18th, 2013

FAKEM RATs Disguise Their Traffic as Yahoo! Messenger to Avoid Detection
Trend Micro has released a white paper that details these RATs
- Security Blog
- By Eduard Kovacs
- November 27th, 2012
PlugX RAT Developers Release New Version, Become More Confident
Kaspersky experts have found that the error logging function has been removed