Earlier this year, Symantec revealed the existence of a sophisticated cybercriminal operation that targeted European organizations, particularly ones from France. Now, experts are providing more details on the attacks which continue to this day.
One of the attacks against a French multinational company, which took place in April 2013, started with a fake email that contained a link to a file, apparently an invoice, hosted on a file sharing service. The email had been sent to a VP’s administrative assistant.
Later, the administrative assistant received a phone call from another VP within the firm who instructed her to process the invoice. The invoice was actually a remote access Trojan (RAT) and the VP was actually a cybercriminal.
Experts warn that cybercriminals are using aggressive social engineering tactics in an effort to defeat the defenses implemented by organizations and their financial institutions.
In another attack observed by Symantec, the crooks installed a RAT on the targeted organization’s systems. Once the malware was in place, they stole disaster recovery plans and details of the company’s bank and telecoms provider.
With this information at hand, the attackers called the telecoms provider, told them that a physical disaster had occurred, and asked for the organization’s phone numbers to be redirected to phones controlled by the cybercriminals.
Shortly after, the cybercrooks called the bank and requested large amounts of money to be transferred to several offshore accounts. When the financial institution called the organization to confirm the transfer, they were actually calling the fraudsters, who, of course, approved it.
In another attack, the cybercriminals needed to use a proprietary in-house system that leveraged a two-factor authentication device to steal the money.
They called one of the employees pretending to be someone from IT staff. The employee was told that maintenance work was needed on the fund transfer system.
The victim was instructed to turn off the monitor for privacy reasons. The employee complied and the crooks easily transferred large amounts of money form the company’s accounts.
In some cases, the crooks don’t even need malware to carry out the attack. In one instance, the fraudsters impersonated a bank employee and sent an email about a system upgrade to an actual bank employee.
The next day, the cybercriminals called the bank employee and asked him/her to perform a “test” wire transfer. Of course, there was no test. The money ended up being transferred to an offshore account.
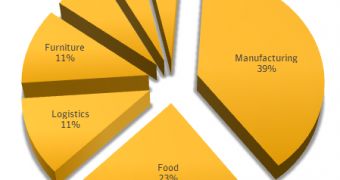
A majority of the victims of this operation, dubbed “Operation Francophoned,” are located in France. Most of them are from the manufacturing sector, followed by food, logistics, and furniture sectors.
 14 DAY TRIAL //
14 DAY TRIAL //