- Security
- By Gabriela Vatu
- February 24th, 2017

Necurs Botnet Gets Proxy Module with DDOS Capabilities
Given the size of the Necurs botnet, if used for DDOS attacks, the damage could be massive, researchers say
- Virus alerts
- By Catalin Cimpanu
- October 24th, 2016
Locky Adds Support for a New "S**T" Extension
New spam campaign has made victims all over the world
- Spam Reports
- By Catalin Cimpanu
- October 20th, 2016

Locky Spam Numbers Go Down as Ransomware Switches to LNK Files
Locky group changes spam & infection technique
- Virus alerts
- By Catalin Cimpanu
- September 30th, 2016

Locky Drops Offline Mode and Switches to New ODIN Extension
Locky offline mode experiment seems to end as ransomware operators revert back to using online C&C servers
- Virus alerts
- By Catalin Cimpanu
- August 26th, 2016

New Locky Ransomware Version Delivered as DLL File
Locky switches EXE binaries for DLL files
- Spam Reports
- By Catalin Cimpanu
- August 18th, 2016

Locky Ransomware Spam Campaigns Switch to Macro-Based Distribution
Dridex spam distribution stops altogether
- Security
- By Catalin Cimpanu
- August 7th, 2016
Security Researcher Tricks Tech Support Scammer Into Installing Locky Ransomware
Infosec researcher has fun at a crook's expense
- Spam Reports
- By Catalin Cimpanu
- July 28th, 2016
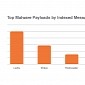
Locky Ransomware Was Top Malware Threat for Q2 2016
Q2 quieter than Q1 thanks to Angler and Nuclear shutdowns
- Virus alerts
- By Catalin Cimpanu
- July 26th, 2016

New Locky Spam Wave Delivers Entire Ransomware Inside JavaScript File
Locky ransomware continues to evolve, gets closer to 100% JS
- Spam Reports
- By Catalin Cimpanu
- May 28th, 2016

Biggest Spam Flood in Years Distributes Locky Ransomware
Spam wave originated from Indian and Vietnamese IPs
- Security Fixes and Improvements
- By Catalin Cimpanu
- April 8th, 2016

Adobe Patches Flash Zero-Day Exploit Used to Deliver Cerber and Locky Ransomware
CVE-2016-1019 used in Magnitude and Nuclear exploit kits
- Security
- By Catalin Cimpanu
- April 7th, 2016
Security Experts Crack Dridex Admin Panel, Recover Victim Data
Security firm turns the table and hacks the bad guys
- Incidents
- By Catalin Cimpanu
- April 5th, 2016

Ransomware Epidemic Makes Two New Victims, Hospitals in California and Indiana
Ransomware infections are out of control, highly-efficient against hospitals, the bigger the hospital, the better
- Security
- By Catalin Cimpanu
- March 10th, 2016

Dridex Botnet Has Replaced Banking Trojan with Locky Ransomware
Group leader's arrest might have forced them to adapt
- Security Blog
- By Catalin Cimpanu
- February 24th, 2016

Locky Ransomware Makes Its First High-Profile Victim As It Continues to Spread
Locky ransomware infects computers at New Zealand hospital
- Security
- By Catalin Cimpanu
- February 17th, 2016

Distributors of Dridex Banking Trojan Take a Break, Deliver Ransomware Instead
A new ransomware family named Locky spreads to 446,000 users thanks to Dridex banking trojan affiliate