- Security
- By Eduard Kovacs
- February 19th, 2013

Mandiant Investigates Chinese Government-Sponsored Hackers – Video
Experts show that the Chinese military is likely coordinating the attacks
- Security
- By Eduard Kovacs
- February 14th, 2013

53% of Professionals Wrongly Believe APTs Are Not Different from Traditional Threats
Global IT association ISACA has released the results of a study sponsored by Trend Micro
- Advisories
- By Eduard Kovacs
- January 22nd, 2013
Cybercriminals Use Legitimate Tools in APT Attacks, Experts Say
Trend Micro experts provide some valuable advice for IT security teams
- Security
- By Eduard Kovacs
- January 4th, 2013

HeartBeat: Advanced Persistent Threat Aimed at South Korean Government
Trend Micro researchers have released a details paper on the threat
- Linux & Opensource Blog
- By Silviu Stahie
- December 13th, 2012

APT Exploit Fixes for Ubuntu 12.10
Other two operating system from Canonical have been affected by the issue
- Security Blog
- By Eduard Kovacs
- December 11th, 2012

Russian Space Research Industry Targeted by Cybercriminals Possibly from Korea
The education, information and telecommunication industries are targeted as well
- Security Fixes and Improvements
- By Eduard Kovacs
- November 6th, 2012

Defining Cyber Defense Strategies for 2013 Is Like a Game of Chess, Experts Say
Trend Micro's Tom Kellerman has released an interesting opinion piece on the matter
- Security Blog
- By Eduard Kovacs
- October 22nd, 2012
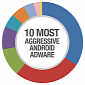
Trend Micro Report for Q3, 2012: Zero-Days, Mobile Malware and Phishing
The number of malicious Android apps has considerably grown in the past months
- Linux & Opensource Blog
- By Silviu Stahie
- October 20th, 2012

APT 0.9.7.6 Officially Released
The latest version of Advanced Package Tool can be downloaded from Softpedia
- Security Fixes and Improvements
- By Eduard Kovacs
- October 9th, 2012

Trend Micro Launches “Custom Defense,” APT Protection and Analysis Solution
The product focuses on detection, analysis, adaption and response
- Virus alerts
- By Eduard Kovacs
- August 25th, 2012
Cybercriminals Hijack Servers Remotely with Hikit APT
The attacker contacts the malware, not the other way around
- Security Blog
- By Eduard Kovacs
- August 9th, 2012
FireEye Study Reveals False Sense of Security Among Professionals Regarding APTs
They want to educate IT staffers on the proper defense mechanisms for advanced threats
- Security Blog
- By Eduard Kovacs
- June 29th, 2012
APT Attacks Rely on New Mac OS X Backdoor to Target Uyghur Activists
Backdoor.OSX.MaControl.b steals files and executes commands on the infected machine
- Interviews
- By Eduard Kovacs
- June 14th, 2012

Softpedia Exclusive Interview: Max Nyman on Advanced Evasion Techniques
Stonesoft representative details the threats posed by AETs
- Interviews
- By Eduard Kovacs
- June 6th, 2012
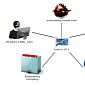
Softpedia Exclusive Interview: Trend Micro Expert on the IXESHE Campaign
Nart Villeneuve, a senior threat researcher, shares their findings and offers some tips
- Security Blog
- By Eduard Kovacs
- May 30th, 2012
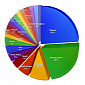
Trend Micro Details IXESHE Advanced Persistent Threat Campaign
The main targets are companies from East Asia and electronics manufacturers
- Security
- By Eduard Kovacs
- April 27th, 2012

EA Security Chief: Networks Hard to Defend Against AETs and APTs
The CISO believes that executives need to become more involved