One of the latest Advanced Persistent Threats (APT) analyzed by security researchers is the campaign known as IXESHE, or i-sushi.
Since Trend Micro has been actively involved in monitoring and mitigating the threats posed by it, we’ve requested further details from Nart Villeneuve, a senior threat researcher, one of the people who has been closely following the APT’s targets and victims.
Softpedia: Please introduce yourself for our readers.
Nart Villeneuve: I am Nart Villeneuve, a Senior Threat Researcher at Trend Micro Inc. where I focus on targeted malware attacks.
I have conducted in-depth investigations of five malware-based espionage networks (GhostNet, ShadowNet, LURID , LuckyCat and IXESHE) and I continue to monitor numerous targeted attack campaigns, or what’s now known as Advanced Persistent Threat (APT) activity, with an emphasis on building threat intelligence by developing indicators that can be used to identify the tools, tactics, and procedures used in targeted attacks.
Softpedia: How did Trend Micro come across the IXESHE APT?
Nart Villeneuve: IXESHE is a long- running campaign that we have been monitoring for some time.
Softpedia: What makes this campaign different from what we’ve seen so far?
Nart Villeneuve: This campaign exhibits the typical behavior associated with an APT campaign: a target receives a socially engineered email that is contextually relevant; the email contains a malicious attachment (or a link to a malicious file) and encourages the reader to open the attachment.
Once opened, the malicious document attempts to exploit a vulnerability in office software (such as Adobe Reader or Microsoft Word) and drop malware on the targets computer. The malware then connects to a command and control server and awaits instructions from the attackers.
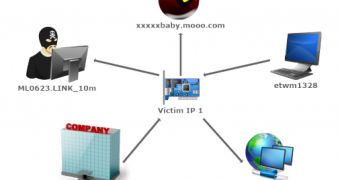
What is unique in the case of IXESHE was the use of internal, compromised computers as command and control servers.
Softpedia: The attackers rely on malicious PDF files to exploit vulnerabilities in Adobe Reader, Acrobat and Flash Player. In order to defend itself against such a threat, would it be sufficient for a company to ensure that these pieces of software are updated at all times?
Nart Villeneuve: Keeping software up-to-date offers some protection, as IXESHE, and other similar campaigns, often use older, reliable exploits in their attacks.
However, IXESHE did make use of at least two “zeroday” vulnerabilities in Adobe products. This means that if a target opened a malicious PDF, the target would be compromised even if fully patched.
Softpedia: Regarding the targets - while two of the categories are from Asia, there’s the German company that seems to stand out. What do you think of this? Is the German firm a random target or is there a particular reason for which it has been attacked?
Nart Villeneuve: The available visibility on targets was limited. Therefore, it is difficult to draw conclusions on targeting beyond what we have stated.
Softpedia: The campaign is currently active. What are the steps taken by Trend Micro and other members of the industry to combat IXESHE?
Nart Villeneuve: We currently discover and block IXESHE command and control servers as well as continue to detect the malicious documents and binaries used by the campaign. We have also developed rules for Deep Discovery that can match specific indicators in IXESHE command and control traffic.
Softpedia: The C&C servers are mostly hosted on compromised machines. What should a company do in order to protect itself against the threat? Please share some advice.
Nart Villeneuve: In addition to detecting and blocking malicious documents, malware components and command and control servers used by the IXESHE campaign, companies should detect IXESHE command and control traffic at the network level using the indicators we’ve provided.
Softpedia: How exactly can Trend Micro help a company in this situation?
Nart Villeneuve: Trend Micro has a deep understanding of the IXESHE campaign and continues to track their attacks as well as their command and control infrastructure.
 14 DAY TRIAL //
14 DAY TRIAL //