A surge in attacks using the PHP-based C99 webshell has forced IBM's Managed Security Services (MSS) team to issue an alert regarding this dangerous threat.
According to security researchers keeping an eye on malicious traffic, during the last two months, traffic that resembles the one seen from the C99 webshell has spiked, with 404 different incidents in February and another 588 in March.
Webshells are files uploaded to a Web server to which attackers make requests or use a special GUI to pass on dangerous commands to the underlying server. They can be coded in various languages, from PHP to ASP.NET, and from JavaScript to Ruby, and despite their separate technical term of webshell, they're nothing more than backdoors, giving attackers control over servers.
If you find pagat.txt on your server, you're probably compromised
IBM says that attackers are leveraging vulnerabilities in unpatched WordPress plugins to infect websites with the C99 webshell.
In its initial infection stage, the actual webshell's code is uploaded to servers in the form of a text file called pagat.txt. In this file, IBM has found obfuscated PHP source code.
To make things even more confusing and infections harder to detect, the attackers don't place this text in the server's root or the vulnerable plugin's folder, but in a theme's directory. IBM says that, in most cases, the pagat.txt file was found at "http://www.website-name.com/wp-content/themes/twentythirteen/pagat.txt".
The actual C99 infection takes place when the attacker finds a way to pass the content of this text file to the server's PHP interpreter. If the malicious code found inside pagat.txt executes, it will do two things.
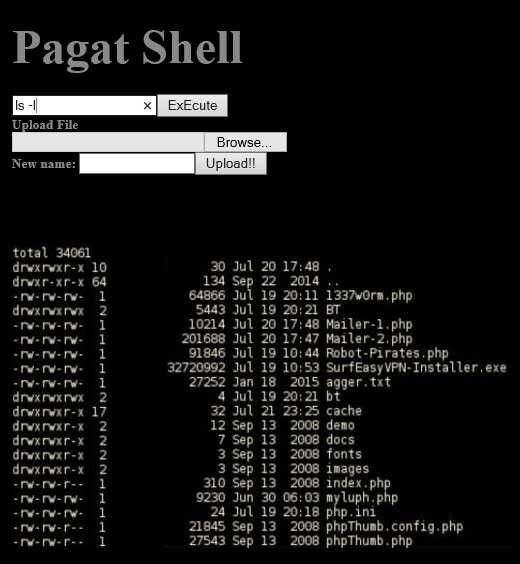
C99 webshell comes with a Web-based GUI
The first is to send an email to the attacker, letting them know the location of their most recent infection. This email is delivered to a Gmail address and contains the website's domain name and the webshell's URL.
The second action taken by the deobfuscated pagat.txt code is to create a new file on the server. This is the actual C99 webshell, which can be accessed by the attacker through their browser at the URL included in the email they have just received.
Pictured below, this webshell allows attackers to run terminal code on the underlying server and also upload new files to the victim's website, possibly more intrusive webshells, DDoS bots, Bitcoin miners, or other server malware.
IBM says that, on April 12, 2016, before going public with their findings, a simple Google search yielded over 32,000 websites where the pagat.txt file was present.

 14 DAY TRIAL //
14 DAY TRIAL //