As expected, the WannaCry ransomware is not even close to being done, despite one researcher discovering a convenient kill switch. Other variants have already been discovered in the wild, some with a different kill switch, some with none at all.
After security researcher going by the Twitter handle MalwareTech discovered that, by purchasing a random domain name, the initial spread of the WannaCry ransomware was stopped, it was expected that the attackers would simply remove this domain from the code, add another or just leave the code free of such an easy way out.
Multiple researchers have confirmed that such variants are available online and coming after Internet users everywhere.
A patched (non recompiled) variant with *NO* kill-switch is out there too. Patched jump and zeroed the URL. See screenshots below. #WannaCry pic.twitter.com/RliIRigXwH — Matthieu Suiche (@msuiche) May 14, 2017"New variants today are now spreading with a modified kill-switch domain. Someone, likely different to the original attackers, made a very small change to the malware so it connects to a slightly different domain. That allowed it to continue propagating again," Chris Doman, security researcher at AlienVault, told us. "Thankfully some researchers are already registering the new domains as they identify them. The cat-and-mouse will likely continue until someone makes a larger change to the malware, removing the kill-switch functionality completely. At that point, it will be harder to stop new variants."
What is WannaCry?
WannaCry is a ransomware that is a lot stronger than other similar malware due to the worm component that helps it spread through networks. This is the main reason why computers in the NHS network went down one after another, or why Renault had to stop production at multiple sites. Once a computer in a network is infected, it's only a matter of time before the rest are too. Other companies have also suffered, including FedEx and Telefonica, as well as Germany's railway system.
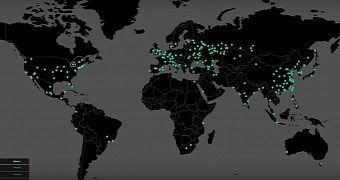
At this point in time, over 200,000 computers have been affected in over 150 countries, despite the kill switch.
The only solution to block this attack is to update your operating system or to make sure you have an anti-malware solution installed to protect you from the malware. Even though this is a nasty ransomware, it's still detectable and, therefore, easy to block.
Microsoft released a patch to fix the vulnerability back in April. This vulnerability was actually exposed by a hacker group called Shadow Brokers who dumped online a series of documents belonging to the NSA which detailed a zero-day exploit. Security researchers warned at the time that it wouldn't be too long before an attack was deployed.
Following the launch of the WannaCry attack, Microsoft went ahead and released a patch for Windows XP and Server 2003, even though both were no longer supported.
 14 DAY TRIAL //
14 DAY TRIAL //