Now that WannaCry infections have dropped somewhat, saviors come to our help, bringing decryption keys. So far, two have been confirmed to work. One is WannaKey, that we've already reported on, and another is WanaKiwi.
Developed by researcher Benjamin Delpy, also known as gentilkiwi, WanaKiwi works on multiple Windows versions, and Europol has also confirmed the decryption tool is effective.
There's a catch before running WanaKiwi, however - you have to keep your machine running after the infection. That means no reboot is allowed. This is because prime numbers may be overwritten in the system's memory after a while, which would lower the chances of the tool being effective.
WanaKiwi works on both Windows XP and Windows 7. "This would imply it works for every version of Windows XP to 7, including Windows 2003, Vista and 2008 and 2008 R2," confirms Matt Suiche from security firm Comae Technologies.
How does it work?
You'll first have to download wanakiwi (obviously). Once you run the file, it will automatically look for the 00000000.pky file and you'll just have to hope for the best while it scans. Basically, you have to hope that your prime numbers haven't been overwritten from process address space, hence why you should not reboot your device after it has been infected.
The tool will not work for every user due to its dependencies, but there's hope for many, many people. There are hundreds of thousands of people who have been infected by WannaCry, and only a handful of those have chosen to pay the $300 in Bitcoin requested by the attackers.
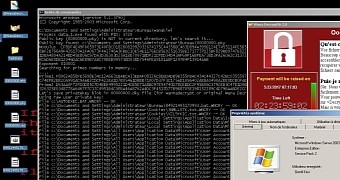
The WannaCry ransomware spread started a week ago and over 220,000 computers have been infected in the process. The malware takes advantage of a Windows vulnerability that was being exploited by the NSA, as per a series of documents dumped online by a hacker group called Shadow Brokers.
Microsoft has released a patch for the affected systems, although users are also advised to install a security solution to block off attacks.
 14 DAY TRIAL //
14 DAY TRIAL //