Independent security researcher Randy Westergren found an information disclosure bug in the United Airlines mobile app, which he reported to the company via its bug bounty program, and he had to threaten the airline with public disclosure to have them fix it, six months later.
The whole affair started back in March, when United Airlines made a big ruckus about its newly launched bug bounty program, unique in its own way, because it rewarded security researchers with air miles instead of money.
Out of curiosity, Mr. Westergren checked out the program and decided to have a quick look over United Airlines mobile app and see if he could quickly spot a bug that he would report.
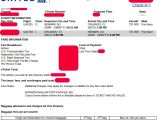
Information disclosure bug in United Airlines' mobile app
He found a flaw inside one of the API calls the mobile app was making, where, if he changed one parameter (mpNumber), he would then gain access to another person's MileagePlus account.
With this knowledge in hand, he was able to access details about his own flights, via a second account he created.
The United Airlines app was revealing personal identifiable information (PII) such as the user's name and location, enough for an attacker to access the victim's reservations via the United Airlines website. From the United Airlines Web portal, attackers could easily extract more personal user data, and even cancel flights if they wanted to.
Details about United Airlines Club Passes were also leaked
Additionally, the same API call also revealed information about a user's United Airlines Club Passes, special sections in the airport where paying United Airlines customers can enter and relax before flights.
One of the things that the API disclosed about Club Passes was the barcode that it got printed on airline tickets. Armed with this data, any attacker could enter inside United Airlines clubs and lounges without triggering any warnings in the system.
Mr. Westergren submitted all these bugs via the bug bounty program in late May, but after seeing that nobody from United Airlines even acknowledged his findings, he sent a last email, warning the company of his desire to go public.
The company fixed the bug this week, before Mr. Westergren's deadline of November 28. Because he threatened to go public, Mr. Westergren was not eligible to receive a reward for his bug.
 14 DAY TRIAL //
14 DAY TRIAL //