Security experts have discovered the first ransomware infections where crooks bundled two ransomware variants in the same file in order to make sure their malware takes root on the user's computer.
After the Petya ransomware had made headlines with its novel approach to encrypting the victim's MBR (Master Boot Record), the crooks behind this ransomware family developed a second, different ransomware variant, which they bundle with Petya for a better infection system.
According to this video from Lawrence Abrams, the crooks behind the Petya ransomware had a big problem, and that's the fact that Petya needed administrative privileges when running.
Mischa is Petya's backup
If users who double-clicked on a file infected with Petya did not allow the ransomware to run with administrator privileges in the UAC (User Account Control) screen that pops up on some computers, the ransomware would fail to execute.
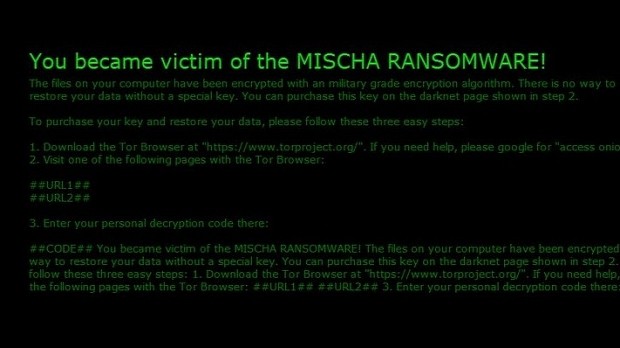
According to MalwareHunterTeam, who made this discovery, recent files that deliver Petya ransomware also include a "ransomware backup" in the form of a new ransomware variant called Mischa.
Micha executes only when Petya fails to get administrative privileges, and works just like any regular crypto-ransomware piece these days, locking files with a powerful encryption algorithm.
Petya + Mischa are part of an upcoming RaaS service
When researching its mode of operation, malware researcher Hasherezade discovered that both Petya and Micha are part of a new RaaS (Ransomware-as-a-Service) platform, currently in beta.
The man behind both malware families, @Janussec on Twitter, is preparing a service that would allow other crooks to rent his ransomware.
The other crooks will only be tasked with distributing the malware. After infecting user PCs, if the victims pay up, the money is split between Janussec and the distributors, according to a pre-arranged payment scheme. The more victims the distributors infect, the more money they get to keep.
Currently, the service is closed down for its beta testing phase, with only a few crooks allowed access to this Dark Web-hosted platform called Janus Cybercrime (James Bond reference).

 14 DAY TRIAL //
14 DAY TRIAL //