Google's Project Zero researcher, Tavis Ormandy, has yet again discovered a security bug in one of the world's leading antivirus engines, this time in Trend Micro's Antivirus for Windows.
According to Mr. Ormandy's findings, when installing the Trend Micro Antivirus for Windows, the company's Password Manager application, which comes bundled with the main antivirus, is also installed.
The application, used as a side feature to the main antivirus, is used to store passwords and works just like any other password manager application.
Trend Micro's Password Manager is written mainly in JavaScript, and it works by starting a Node.js server on the local computer every time the main antivirus starts.
RCE bug allows total system compromise
As Mr. Ormandy discovered, this server opens multiple HTTP RPC ports for handling API requests coming from other applications querying or interacting with information stored in Trend Micro's Password Manager.
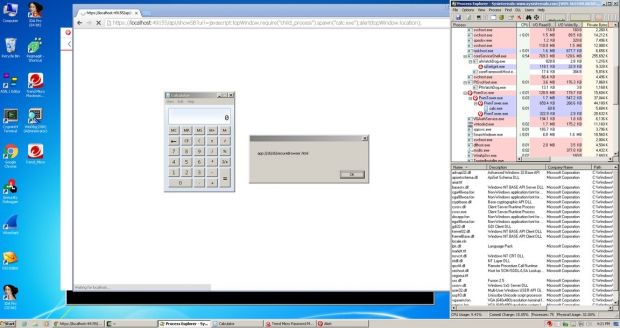
Available at "http://localhost:49155/api/", Mr. Ormandy discovered that attackers could craft malicious links that, when clicked by a user that has a Trend Micro antivirus installed, would allow a malicious party to execute arbitrary code on the local computer.
Depending on the hacker's skill level, various level of attacks can be carried out via this entry point.
Besides reporting the issue to Trend Micro's team and helping them create a patch for this issue, Mr. Ormandy also discovered that the Trend Micro Password Manager also exposes around 70 APIs through this same Node.js server.
Leaky Password Manager is leaky
During his research, he was able to steal encrypted passwords from the password manager application, expose the domains for each encrypted password entry, and also decrypt passwords, using one of the exposed Node.js APIs, responsible for decrypting passwords inside the Password Manager application itself.
Theoretically, an attacker could create a malicious link that chained all these exploits. The attacker would only have to send this malicious link via email, or embed it in a Web page, which if clicked by a Trend Micro user would steal all his passwords and send them to a remote server, under the attacker's control.
No details were given about which Trend Micro Antivirus and Password Manager versions were vulnerable, but a new release has been put out to fix these flaws, so just update your Trend Micro Antivirus to the latest version.
Previously, Mr. Ormandy has discovered security issues in other antivirus engines like AVG, FireEye, Kaspersky, Avast, and ESET.
UPDATE: Trend Micro has published a response to the recent vulnerability disclosure.

 14 DAY TRIAL //
14 DAY TRIAL //