The 19-year-old WinRAR vulnerability that was discovered last month is actively being used by hackers to distribute malware and compromise Windows devices, according to an advisory published by security vendor McAfee.
The bug, which is tied to the ACE implementation in WinRAR, was already patched with version 5.70, so users are recommended to update the file compression tool as soon as possible.
But as noted by McAfee, Windows hosts where the latest version hasn’t been installed just yet are being targeted by an increasing number of exploits that are based on the ACE flaw.
“In the first week since the vulnerability was disclosed, McAfee has identified over 100 unique exploits and counting, with most of the initial targets residing in the United States at the time of writing,” the security company explains.
Patch, patch, patch!
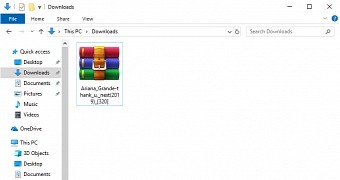
One of the exploits tries to trick people into downloading the malicious payload by using a bootlegged copy of Ariana Grande’s album called “Thank U, Next.” The file is distributed as Ariana_Grande-thank_u,_next(2019)_[320].rar, and it uses a very simple approach to compromise the host.
“When a vulnerable version of WinRAR is used to extract the contents of this archive, a malicious payload is created in the Startup folder behind the scenes. User Account Control (UAC) does not apply, so no alert is displayed to the user. The next time the system restarts, the malware is run,” McAfee explains.
The easiest way to remain protected against these exploits is to install the latest version of WinRAR, which has removed the ACE module entirely. If patching isn’t possible due to various reasons, users should just avoid opening archives coming from untrusted sources and to always keep their anti-malware definitions up to date.
There are obviously no specifics on the number of users that might have been infected, but for now, updating to the latest version of WinRAR should be a priority for everyone.
 14 DAY TRIAL //
14 DAY TRIAL //