An APT group nicknamed StrongPity has put a lot of effort into a recent campaign that has targeted users of encryption software such as TrueCrypt and WinRAR.
Kaspersky Lab says the group had been active in past years, but it employed mostly zero-days to compromise targets and spy on users and their activities.
The most recent attacks, detected in the summer of 2016, relied on new tactics, which the group had never used before.
Group targeted encryption-savvy users
Kaspersky says the group used watering hole attacks and poisoned installers to reach the computers of users that are generally harder to compromise because they use encryption software. It is exactly this penchant for encryption on the victim's side that the attackers focused on.
The group has targeted two encryption software packages in different attacks. The first is WinRAR, a software package known best for its archiving capabilities, but which also comes with a feature that allows users to encrypt data using the AES algorithm and lock it inside a password-protected RAR file.
The second is TrueCrypt, a full-disk encryption utility that locks all files on a hard drive. This software package was very popular two years ago, but most users abandoned it when its developers said the software was insecure and urged them to use other utilities instead.
By targeting users of these two software packages, StrongPity is trying to compromise users that it couldn't compromise before, due to the fact they protected their data.
Group tricked legitimate websites into linking to their malware
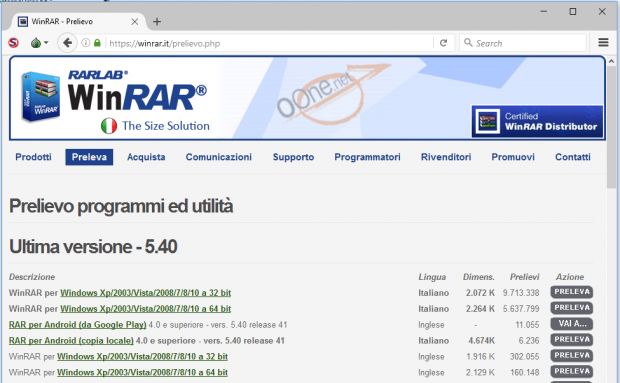
Kaspersky says that StrongPity registered a lookalike domain ralrab.com, which is very similar to the official rarlab.com website, through which WinRAR devs distribute their software.
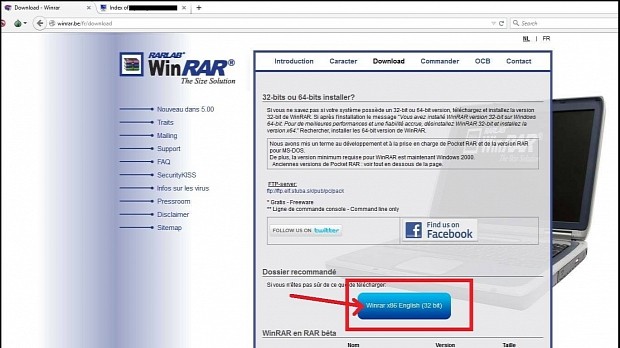
Using this fake domain, the APT managed to trick the operators of the winrar.be website to link to their malicious version of WinRAR on the ralrab.com website, instead of the official one. Their version of WinRAR came with a backdoor trojan, allowing the StrongPity actors to spy on anyone who installed this tainted package.
They pulled the same trick with the winrar.it website, but instead of linking to the ralrab.com website, the group convinced the winrar.it website to host a malicious version of the file themselves.
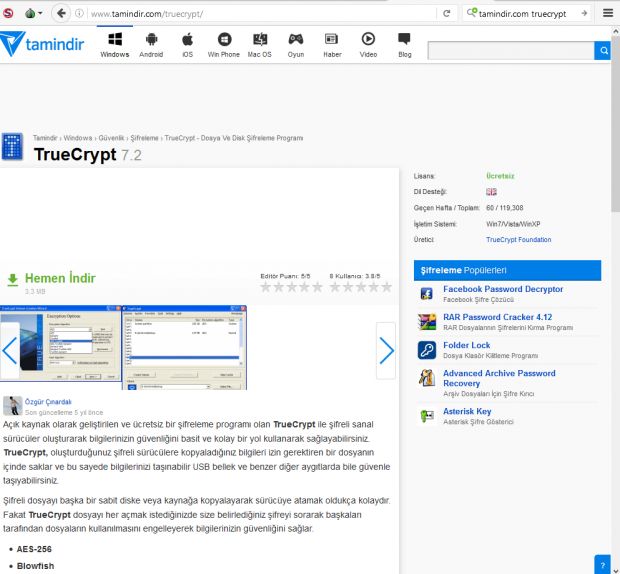
These two incidents took place in May 2016, but the group didn't stop here, and by September 2016, they also managed to trick operators of the Tamindir software downloads website to redirect users who wanted to install the TrueCrypt software to the true-crypt.com website, controlled by the attackers.
Just like with WinRAR, the version of TrueCrypt distributed through this website contained a backdoor trojan that allowed crooks to access the user's system, steal, or intercept data.
Because the trojans were shipped inside the WinRAR and TrueCrypt packages, the attackers had access to encrypted data, which they didn't have in past attacks.
According to Kaspersky, the attacks compromised users in Italy, Turkey, Belgium, Algeria, and France, but traces of the StrongPity backdoor trojan were detected all over Europe, Africa, and the Middle East. Researchers say that over 1,000 systems appear to have been compromised in recent StrongPity attacks.
 14 DAY TRIAL //
14 DAY TRIAL //