Malvertising operations are usually exposed after a few days, but a recent campaign has managed to go undetected for about three weeks before being uncovered by Malwarebytes researchers.
Technically, the campaign is no different from other similar malvertising campaigns, but researchers did observe that fake but clean ads were used in getting the advertising spots, some of them on very famous websites.
According to Malwarebytes, the malicious ads were spotted on sites like ebay.co.uk, drudgereport.com, answers.com, wowhead.com, ehowespanol.com, legacy.com, newsnow.co.uk, talktalk.co.uk, manta.com, and a slew of adult-themed websites.
The monthly traffic of all these websites added up to around 487.4 million active visits, which is right up there with this year's biggest campaigns, if not the biggest.
Ad networks did not properly screen advertisers
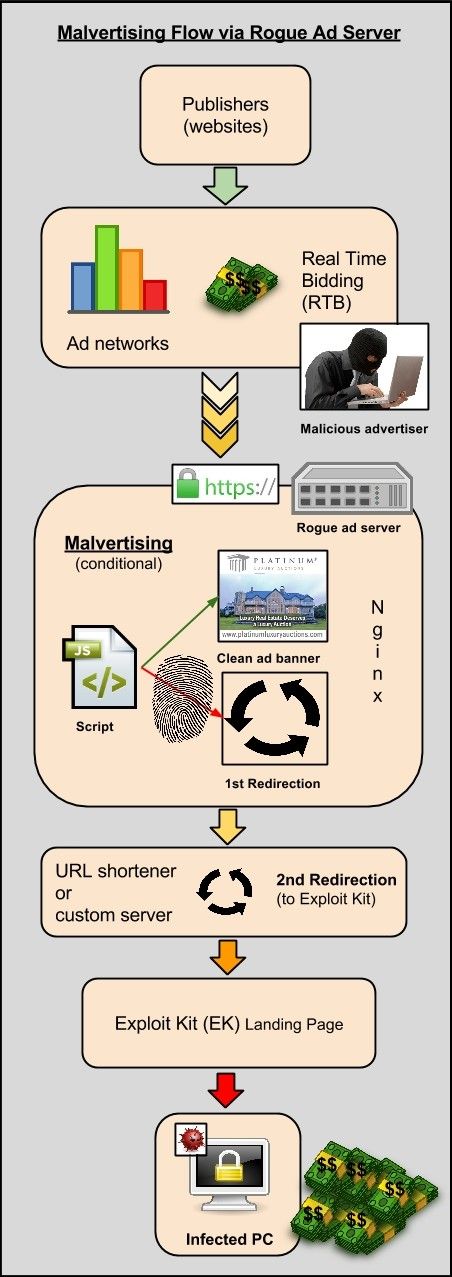
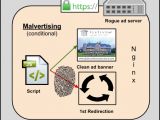
As the researchers explain, the malvertisers followed regular advertising protocol, registering on various ad networks, and submitting clean fake ads to real-time bidding from people looking for ads on their site.
The clean ads got picked up by website owners, who were not aware that their ad network allowed for these ads to be delivered from the malvertiser's own server, via an encrypted HTTPS connection.
By doing so, the malvertiser was able to disguise their traffic, and using a combination of multiple URL redirects and URL shorteners, eventually landed some of the website's visitors on a page where the Angler Exploit Kit was hosted, infecting users with ad fraud and ransomware.
Most infected users were from the US (46%), followed by the UK (36%), Australia (6%), Canada (6%), and Poland (6%).
"This particular case is a good illustration of why screening advertisers is so important, especially when they are allowed to host and serve the ad content themselves," say the Malwarebytes researchers. "The ad could be clean or booby-trapped, but the rogue actors are in full control of the delivery platform and can instruct it to perform nefarious actions that will easily bypass most security checks."

 14 DAY TRIAL //
14 DAY TRIAL //