A recent spam campaign is targeting German-speaking users, spreading malicious Office documents that end up installing a rogue certificate and a copy of the Ozone RAT (Remote Access Trojan).
What's different about this spam campaign is that it doesn't deliver macro-laced Office documents like most spam does these days, but uses an older technique not seen for some time.
Instead of asking users to turn on macros support in their Office applications, victims are asked to double-click on a thumbnail image, which loads and executes malicious JavaScript.
Using JavaScript to download PAC files, rogue certificates, and RATs
This JavaScript file installs a local PAC (Proxy Auto-Config) file that hijacks the user's local Internet connection proxy settings and then downloads a rogue Comodo certificate, which it will use for MitM attacks, later on, to disguise and sign malicious traffic.
Crooks also use another non-standard technique by downloading the malicious PAC file from a TOR URL via a Tor2Web proxy service like onion.to.
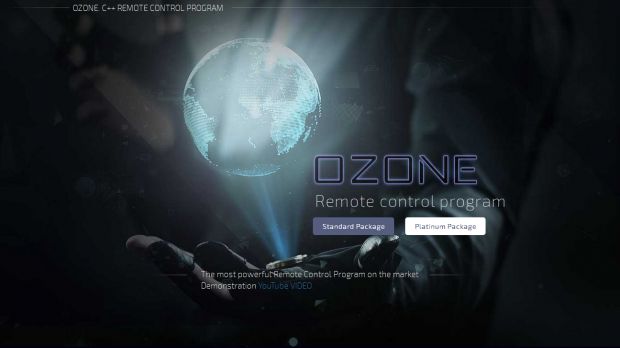
The last thing the JavaScript rogue script downloads is a copy of the Ozone RAT, which first appeared over a year ago and is currently sold online for $20 (standard package) or $50 (platinum package).
Ozone RAT helps crooks connect to their targets
Crooks install the Ozone RAT on the user's device so they could connect to the local copy and take over their workstation in search of valuable information.
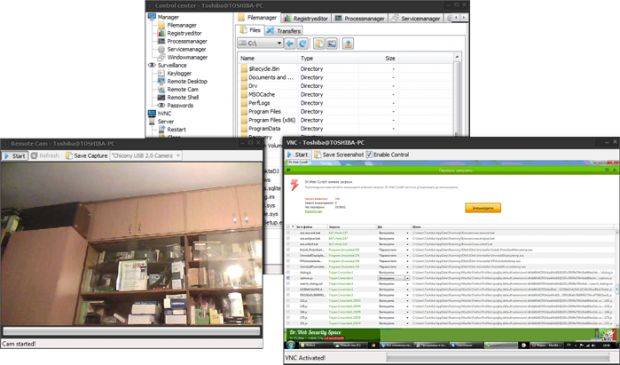
According to Ozone's website, which claims to offer a "legal" remote control product, Ozone comes with a keylogger, a password dumper, a hidden startup routine, the ability to hide its process, the ability to download and execute other files, and a remote desktop feature.
Ozone also comes with its own file manager, a process manager, an application manager, a boot persistence feature, and the ability to access the remote PC's webcam.
The not-so-legal RAT
All "legal" features, which coincidentally are also the features you'll find in spyware programs. But hey, who are we to judge?!
"With RAT applications like Ozone, one does not need to be an expert to create and distribute malware," Fortinet's Floser Bacurio Jr. and Joie Salvio note. "Anyone can buy Ozone from their websites, or simply download 'modified' versions."
"Just a few words of caution, though," the two researchers warn. "This can be a cunning ordeal. These 'modified' versions may be the malware themselves. With a lack of understanding how malware schemes work, even before starting your first attack, you may inadvertently become one of the first victims," the two researchers say, referring to modified Ozone RATs that come with a keylogger to spy on the people wanting to deploy the malware.
UPDATE: The new "double-click thumb image to execute malicious JS" caught the eye of Microsoft's security team as well, who also put out a report just hours after Fortinet's discovery.

 14 DAY TRIAL //
14 DAY TRIAL //