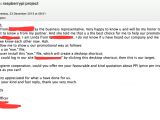
Liz Upton, the Director of Communications for the Raspberry Pi Foundation, has tweeted out a screenshot of an email where an unknown person has proposed that the Foundation install malware on all of its devices.
In the email, a person named Linda is proposing Mrs. Upton an agreement where their company would provide an EXE file that installs a desktop shortcut that, when clicked, redirects users to a specific website. (Raspberry Pi devices can run Windows as well, not just Linux variants.)
Linda from company Q[edited] is also inquiring Mrs. Upton about the Foundation's PPI (Price per Install).
Judging from the lack of proper English used in the email, which is rare for Business Officers, as Linda claims to be, the email is surely from a person not associated with a professional firm.
There are many companies that function as intermediaries between malware distributors and legitimate businesses, either masquerading as advertising agencies or PR firms.
Just two weeks ago, a report from Digital Citizens Alliance and RiskIQ came out and estimated that torrent site operators made $70 million / €63.8 million per year from distributing malware to their visitors, either in the form of malvertising or infected torrent files.
Companies tied to the open source community don't fall for these emails
With the Raspberry Pi Foundation boasting a userbase five million strong, malware distributors are certainly drooling over the chance of having their malicious code hidden somewhere in the firmware of one of the hottest gadgets on the market right now.
Raspberry Pi, the low cost, credit-card sized computer that's been powering the Internet of Things (IoT) market, would allow hackers access to a much safer environment to operate from.
Since there is currently no security software that can run on IoT devices, a malware infection can linger for years or until someone wipes the firmware, which is extremely rare in production environments.
If the Raspberry Pi Foundation weren't so close to the Linux Foundation and its principles of openness and community-built software, we would probably have something to worry about.
Editor's Note: There have been discussions on social media about how most Raspberry Pi devices normally run Linux, where EXE files don't work. This doesn't matter. The email was obviously sent by a person with no technical skills. The point of the article is to highlight how malware distributors are in a constant search for new clients where they can place their malicious payloads, not to discuss the technical inaccuracies in the email itself.
Amazing. This person seems to be very sincerely offering us money to install malware on your machines. pic.twitter.com/1soL0MIc5Z
— Raspberry Pi (@Raspberry_Pi) December 23, 2015
 14 DAY TRIAL //
14 DAY TRIAL //