A relatively new banking trojan is relying on gullible users to gain admin rights on Android 6 devices, proving that, no matter how much Google tries to secure its OS from malware, humans will always gladly open the door for dangerous infections.
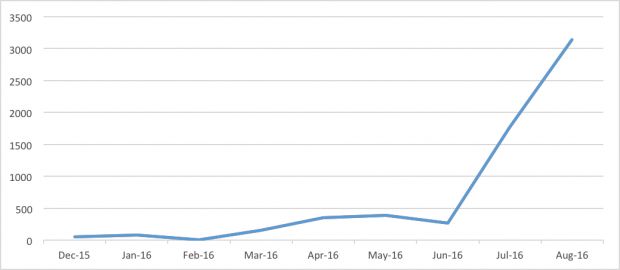
Named Gugi (Trojan-Banker.AndroidOS.Gugi.c), this banking trojan discovered by security researchers from Kaspersky appeared in late 2015, and it is currently extremely active in Russia, with 93 percent of all infected victims living in the country.
Gugi trojan spread via SMS spam
Gugi, which is spread via SMS spam that passes as a classic "You received an MMS" alert, contains an infection routine specifically adapted for Android 6 and its security measures such as its multi-level app permissions systems.
When users install Gugi on their smartphones, they'll be greeted by a very simplistic window, with no details except the text: "Additional rights needed to work with graphics and windows."
Tapping the "Provide" button brings up the real Android permissions popup, which doesn't ask for "rights to work with graphics and windows," but it's actually a permission request to allow Gugi to draw overlays on top of other apps.
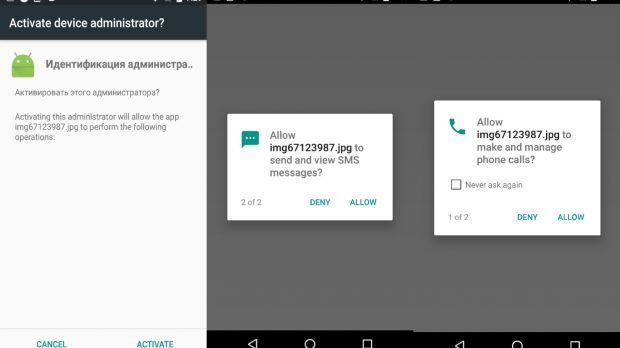
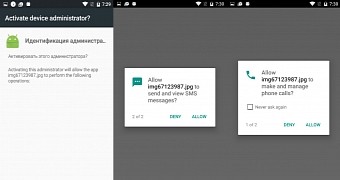
Trojan shows a barrage of app permission popups
The ability to draw over other apps is all the Gugi authors wanted in this incipient stage. With this permission in hand, Gugi will then block access to the user's screen by showing overlay after overlay.
During all these subsequent screens, Gugi will ask for more and more permissions, all needed to power its malicious activity. Also mixed somewhere in there is the trojan asking for administrator privileges.
The only way to dismiss these screens is if the user grants the permissions Gugi asks for, the trojan bombarding the user with more overlays until it gets what it wants.
Gugi collects user credentials, credit card numbers
This is also the stage where users have a chance of preventing further damage. Users can still boot the device in safe mode during this phase and uninstall the trojan before it manages to get admin privileges. If Gugi gains admin privileges, the uninstallation procedure will be much harder.
If users give in and grant Gugi all the permissions it asks for, the trojan will be able to overlay fake login forms over other apps such as those used for mobile banking, and collect user credentials.
Kaspersky also says Gugi overlays a fake form on top of the Google Play Store app and asks users to enter their credit card details. This type of behavior is the norm for Android banking trojans, which all operate in the same way.
While Google has plugged many bugs in the Android 6 and 7 OS source code that allowed crooks to elevate their malicious apps to the phone's root level, it appears that there's still no answer to social engineering attacks that target the phone's user.
 14 DAY TRIAL //
14 DAY TRIAL //