Exploit developer and vulnerability researcher Sergey Zelenyuk decided to publicly disclose a Virtualbox zero-day vulnerability and the exploit that goes with it because of disagreeing with the current state of bug bounty programs and security research.
As detailed in his GitHub-based disclosure, the security issue chains multiple bugs and it affects all VirtualBox virtual machines with the requirement of them using the default configuration that sets the network card to Intel PRO/1000 MT Desktop (82540EM) and the networking mode to NAT.
Moreover, the zero-day also affects all possible combinations of guest or host operating systems running inside the targeted virtual machines.
Following successful exploitation of the zero-day Virtualbox vulnerability, attackers can gain elevated privileges on the target system allowing for an escape from the guest operating system running in the virtual machine to the host OS.
The zero-day allows attackers to escape the guest and escalate privileges to ring 0
"The E1000 has a vulnerability allowing an attacker with root/administrator privileges in a guest to escape to a host ring3," says Zelenyuk. "Then the attacker can use existing techniques to escalate privileges to ring 0 via /dev/vboxdrv."
According to the security researcher, the exploit he describes in detail in his write-up is 100% reliable and "it either works always or never because of mismatched binaries or other, more subtle reasons I didn't account."
"Until the patched VirtualBox build is out you can change the network card of your virtual machines to PCnet (either of two) or to Paravirtualized Network. If you can't, change the mode from NAT to another one. The former way is more secure."
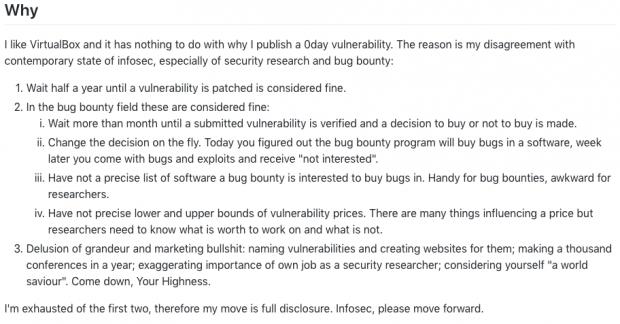
Zelenyuk started his write-up by detailing the reasons behind the public disclosure of the vulnerability and exploit, with a previously discovered Virtualbox security issue he disclosed to Oracle and was fixed in 15 months probably being the catalyst behind his decision.
His statement in full:

 14 DAY TRIAL //
14 DAY TRIAL //