With the proliferation of Internet-connected fuel tanks in modern gas stations, the lack of proper security measures can lead to future disasters, Trend Micro security researchers claim.
Presenting their most recent research at the Black Hat USA 2015 conference in Las Vegas, Kyle Wilhoit and Stephen Hilt of TrendLabs Forward-Looking Threat Research (FTR) Team have revealed their GasPot experiment.
As they put it, this was a honeypot to test and see how interesting Internet-connected gas tanks were to today's hackers.
Their experiment relied on creating fake gas tanks that mimicked Guardian AST gas-tank-monitoring systems, which were under a series of mysterious attacks at the start of 2015.
GasPot, the honeypot for gas tank-loving criminals
These fake tanks, nicknamed GasPot (as in GAS tank honeyPOT), were mere servers that were configured to spoof the terminal of a real-life gas tank but that also contained a Python script that logged its activity.
They were specifically designed to deliver fake gas tank data, while also watching for any commands someone might try them feed it through their Internet-accessible terminal.
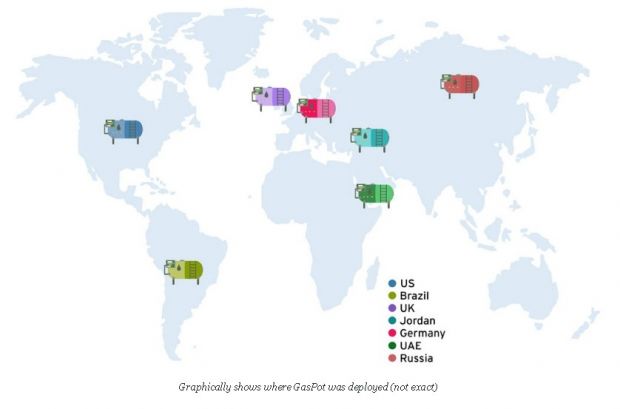
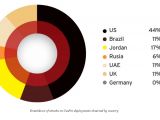
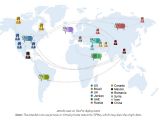
GasPot instances were deployed in several countries like the US, Russia, Germany, Brazil, Great Britain, the United Arab Emirates, and Jordan.
According to Trend Micro's research, hackers bought into their experiment, and soon, underground forums and text snippets on Pastebin were popping up as hackers shared information with each other.
As data collected in the logs, The Trend Micro team observed that the most predominant activity was of basic GET commands, used to query for information about the gas tank, generally used by automatic scanners.
One gas tank was DDOSed
That didn't hide the fact that several commands were actually entered in the gas tank honeypots, like the ones that list the tank's basic details and the ones that change its name.
Some gas tanks had their name changed, but the weirdest finding was that, at one point, a 2Gbps DDOS (distributed denial of service) attack was recorded on one of the GasPot instances located in Washington, preliminary evidence showing the Syrian Electronic Army (SEA) as being at its source.
The researchers did claim that they "have not seen the SEA use this technique in previous attacks," and this "could have been performed by another group or person who wants to put the blame on the SEA."
US gas stations were the most targeted ones
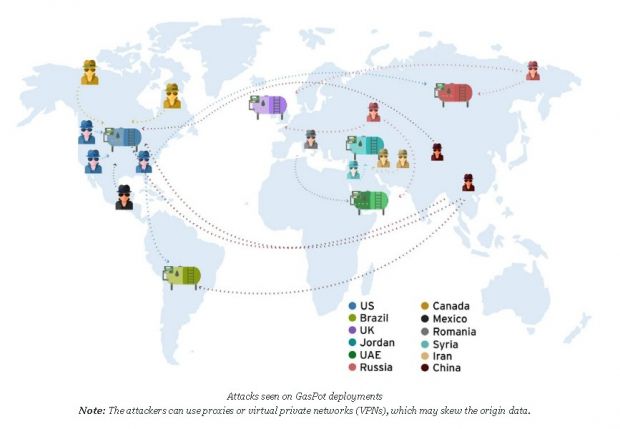
The logs revealed that most of the attacks originated from countries like the US, Canada, China, Iran, Russia, Mexico, Romania, and Syria, but these details should be taken with a grain of salt, since most of them used secure VPN connections and were probably hiding their true location.
The most attacks were recorded on gas tanks found in the US (44%), followed by Jordan (17%), Brazil, Great Britain, and the United Arab Emirates (all with 11%).
Taking over a gas station's tanks is not glamorous as hacking the Pentagon email, but an attacker could easily monetize their efforts by extorting the owners for money if they manage to lock down the pumps.
Additionally, unprotected gas tanks can also be weaponized, feeding operators erroneous data, which can easily lead to accidents like the one in Bayamon, Puerto Rico in 2009.

 14 DAY TRIAL //
14 DAY TRIAL //