A sophisticated phishing campaign targeted the employees of six Russian banks, distributing the Ratopak malware, a spyware variant that allowed its operator to take control of infected systems and spy on its targets.
According to Symantec's security researchers, the campaign took place in December 2015, but they also recorded a campaign with similar characteristics during the month of October, yet unconfirmed.
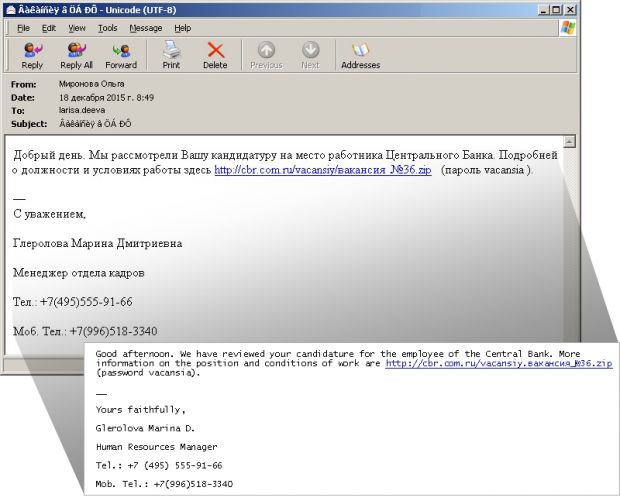
For the December attacks, attackers tried to trick employees using emails that were sent from a domain that looked like the authentic Central Bank of Russia website (cbr.ru).
The attackers registered the cbr.com.ru domain and used it to send fictitious job offers to the target bank's employees, luring them into accessing a link embedded in the email's body.
This URL pointed to a Web-hosted ZIP file, which, when downloaded and decompressed, would install the Ratopak trojan.
Symantec noticed that, besides the obviously fake cbr.com.ru domain, the attackers made another mistake that also gave them away. The sender's name in the email "From to:" field was different from the name used in the signature at the end of the email.
Attackers were infecting bank employees with the Ratopak malware
As for Ratopak, researchers say that this is a very powerful and intrusive piece of malware. Ratopak can log keystrokes, take desktop screenshots, get clipboard data, and download other files or even malware on infected computers.
To hide the data it was stealing, Ratopak would also use domains that included the "buh" term, which means "accountant" in Russian. The malware would send data to these domains, hoping that admins filtering outgoing traffic would think it was the URL of an accounting or financial service.
In previous reports by other cyber security firms, Ratopak was also used against the accounting departments of various Russian businesses. For reference, ESET identified this threat under the Buhtrap codename.
Curiously enough, Ratopak included a filter in its source code that would terminate the trojan's execution if the computer's language was other than Russian or Ukrainian.
This led Symantec researchers to believe that the campaign's operators were also Russians, who tried to steal insider information or tax-related details.

 14 DAY TRIAL //
14 DAY TRIAL //