Cyber-espionage groups linked to the Russian government often use Microsoft Windows, Office, and Internet Explorer exploits to compromise their targets, according to a study of past cyber-incidents going back to January 1, 2012.
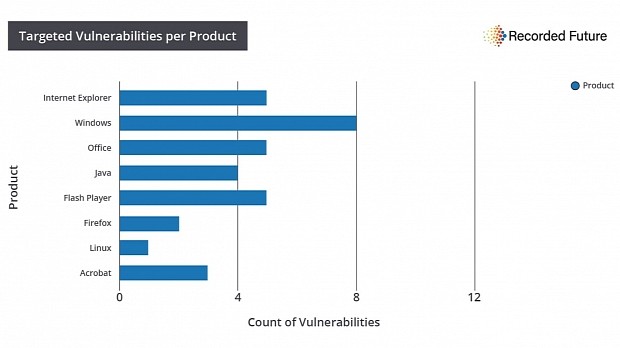
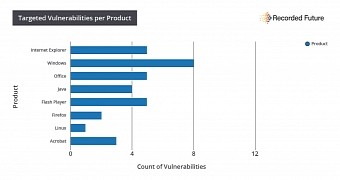
Microsoft was clearly the groups' favorite vendor, with 54 percent of all exploits targeting the company's products.
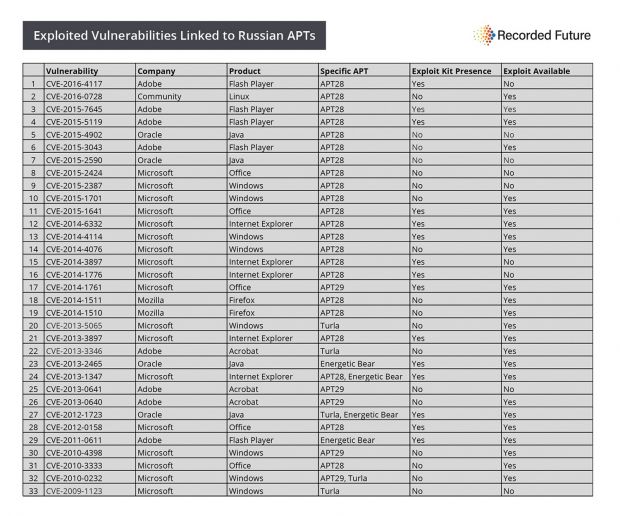
Following a study of all APT attacks between January 1, 2012, and July 31, 2016, the team at Recorded Future found that Russian APTs have eight Windows vulnerabilities in their arsenals; five exploits for each of Internet Explorer, Office, and Flash Player; four for Java; three for Adobe Acrobat; two for Firefox; and one for Linux machines.
Russian APTs do not share vulnerabilities
Only three of the total 33 vulnerabilities used in past attacks overlapped in the arsenal of two APTs. Most cyber-espionage groups did not share hacking tools and researched and managed their separate set of vulnerabilities.
As security vendors unmasked their attacks and the vulnerabilities were fixed and entered the public domain, 46 percent of these security flaws made their way into exploit kits used by regular cyber-crime gangs.
Fortunately, not all of the 33 vulnerabilities have been weaponized, at least in the eyes of the public. Recorded Future researchers found that only 73 percent of these security flaws had been converted into publicly available exploits, delivered via sites such as GitHub, ExploitDB, or tools like Metasploit.
Data from four APTs included
The Recorded Future research factored data from the four APTs for which several researchers have discovered possible links to Russian state organizations.
These are APT28 (Fancy Bear, Operation Pawn Storm, Strontium, Sednit, Sofacy, Tsar Team), APT29 (Cozy Bear, The Dukes, Office Monkeys), Energetic Bear (Crouching Yeti, Dragonfly, Group 24, Koala Team), and Turla (Epic Turla, Snake, Ouroboros, Carbon).
The most active and proficient of these was APT28, owner of 27 of the 33 vulnerabilities. On the other side, Energetic Bear only used publicly available exploits (at the time of their attacks), and it doesn't seem to invest in searching for zero-days, but merely grabs exploits off the Internet.
The way these APTs deployed their hacking tools seems to follow the same pattern. The groups used spear-phishing emails with malicious file attachments, or links inside emails leading victims back to sites hosting watering-hole or phishing pages.
 14 DAY TRIAL //
14 DAY TRIAL //