Security researchers have found a ransomware family that can securely encrypt files, even if the victim does not have an Internet connection.
In the old days, ransomware usually blocked access to a computer's screen by showing a fullscreen message that was hard to remove. The first stage of evolution was when ransomware started encrypting the user's files, but this type of malware was not efficient because it had to store the encryption key somewhere on the PC. Antivirus companies simply reverse-engineered the encryption keys and then provided ransomware removal tools.
This changed in recent years, when ransomware operators began leveraging Internet connections to encrypt the user's file and then send the encryption key to one of their C&C servers. If the user wanted access to their files again, they had to pay a ransom.
Return of the "offline" ransomware
Check Point researchers are now reporting on a new ransomware family that manages to encrypt files without storing the entire decryption key locally, despite the lack of an Internet connection.
"The encryption functionality is built with several layers of encoding and encryption, including two separate levels of RSA," say Check Point security researchers. "Due to this functionality, the ransomware is able to encrypt all files locally without connecting to a C&C server."
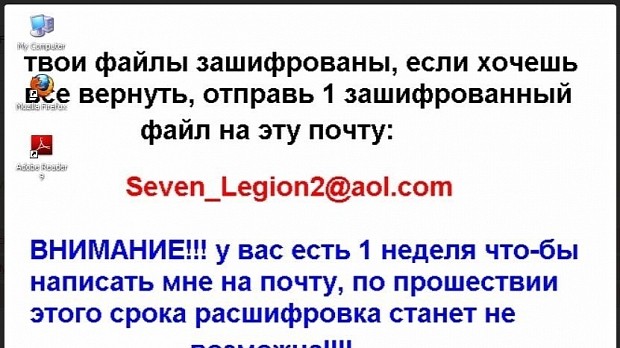
The ransomware does this by generating a local RSA public key that it uses to encrypt files, which it then stores in the metadata of each file. When a victim wants their data decrypted, they can contact the ransomware's operators via email (added to the name of each file), and send one of the encrypted files as an attachment.
The ransomware operator looks at the file's metadata, extracts the user-side-generated RSA public key, and matches it to their own RSA private key database.
Cracking the ransomware's encryption would take 2 years
Check Point's staff stated that it was not feasible to brute-force the ransomware encryption. Embarking on such a task would take around two years, and only if using a large computer cluster, which many home users don't have access to.
As the researchers say, this is one of those cases the FBI was talking about when it said it was sometimes better to pay the ransom.
For this particular ransomware family, the ransom is 20,000 Russian Ruble ($300). Yes, your intuition is right: the ransomware was created by Russian-speaking hackers.
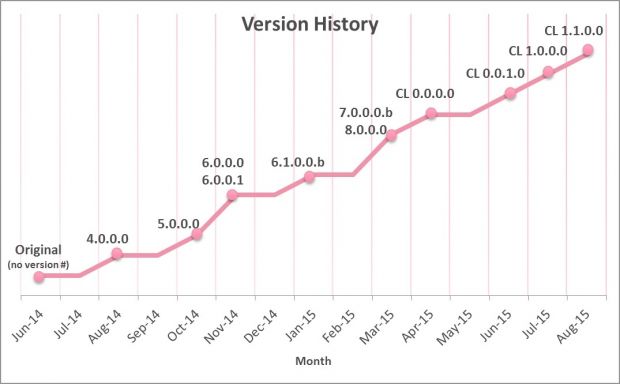
After some further digging into this matter, Check Point staff managed to discover traces of this particular ransomware dating back to June 2014. Antivirus companies previously detected it under different names:
- Win32.VBKryjetor.wfa (Kaspersky)
- Ransomcrypt.U (Symantec)
- Ninja Ransomware (Enigma Software)
- Troj/Agent-AOTR (Sophos)
- Troj/Drop-HQ (Sophos)
- Troj/Ransom-AZT (Sophos)
- Troj/Ransom-BGX (Sophos)
- Troj/Ransom-BJQ (Sophos)
- Troj/Ransom-BJV (Sophos)
- Troj/Agent-ANBL (Sophos)
- Troj/Ruftar-H (Sophos)
- Troj/VB-IHK (Sophos)
- Mal/Delp-AI (Sophos)
 14 DAY TRIAL //
14 DAY TRIAL //