Security flaws in traffic sensors installed all over Moscow could pose serious problems for smart cities in the coming years, Kaspersky's Denis Legezo has discovered.
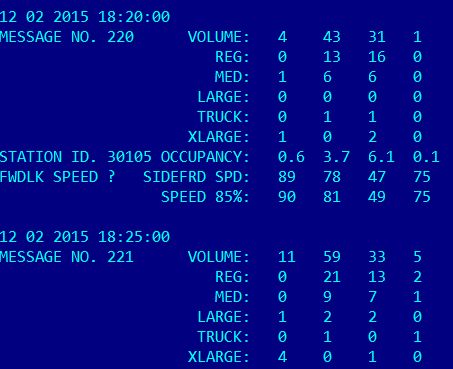
Mr. Legezo has conducted a series of security tests of Moscow's road traffic sensors system, which authorities employ to record the speed, size, and flow on each street lane.
The information these sensors gather is relayed to a command center, where it is used by other smart traffic systems to manage traffic lights, close roads, or issue traffic jam warnings.
Researcher mapped Moscow's entire traffic sensors network
The Kaspersky researcher discovered that the traffic sensors deployed around Moscow could be mapped thanks to their Bluetooth connections.
The researchers created custom software to record the MAC address of each sensor, its geographical position, and a friendly text that exposed clues about its vendor make and model.
He then jumped in a car and slowly drove all around Moscow, mapping sensors installed on poles around the city, inside easy-to-spot white boxes.
Besides the open Bluetooth connection used to communicate data to the Center for Road Traffic Management, the researcher also found a local WiFi connection, which he could use to alter the firmware of some devices to expose and even alter collected traffic data.
Smart cities aren't that smart when hackers tinker with their data
His findings will once again fuel critics of IoT "smart" cities, which, despite their advantages, also come with new risks that could lead to catastrophic situations.
In this case, an attacker could have altered traffic lane statistics, data based on which authorities could have decided to close roads or redirect traffic to other routes, eventually leading to enormous traffic jams all over the city.
But obviously, there are also advantages to living in smart cities. The researcher doesn't take a stance against this kind of technology but advises cities around the world to pay more attention when selecting, configuring and deploying these types of devices.
"At the installation stage, it makes sense to avoid using any standard identifiers," Mr. Legezo concluded. "Obviously, manufacturers need to advertise their products, and the servicing teams may need to collect additional information from the adhesive labels on a device, but besides the convenience there are also issues of information security to consider."
The researcher also recommends that authorities rely on an additional layer of proprietary protection layers, on top of the standard identification implemented in well-known protocols, with the aim of making an attacker's job more difficult and time-consuming, and maybe enough to deter him.
Mr. Legezo presented his work at this year's RSA US 2016 security conference. A copy of his presentation can be downloaded from here.

 14 DAY TRIAL //
14 DAY TRIAL //