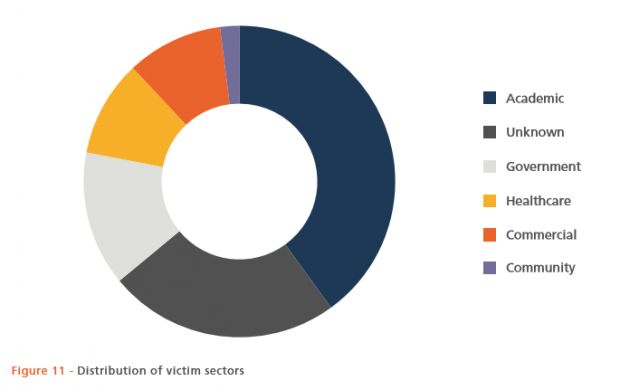
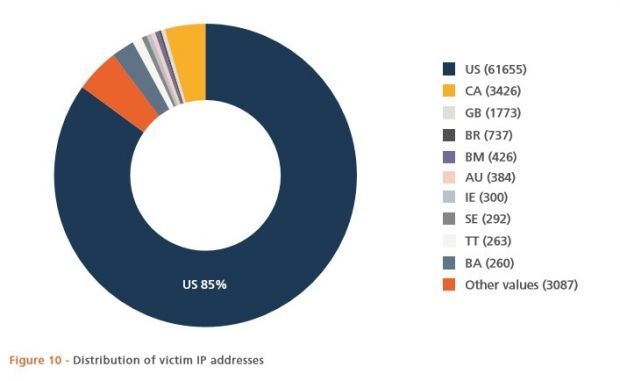
Security experts from BAE System have discovered a new version of the Qbot malware that's more sophisticated than ever before, actively targeting public institutions, mainly located in the US, such as universities, schools, government networks, and healthcare organizations.
The Qbot malware, also identified by various other cyber-security vendors as Qakbot, was first discovered in 2009, when its operators started distributing it with the aim of stealing user credentials, creating backdoors on infected devices and establishing a world-spanning botnet.
Activity from this botnet has been relatively quiet, compared to other bigger botnet operators, but spikes have been seen every time the malware is updated with a new feature.
Qbot uses modern polymorphism techniques to avoid AV detection
According to BAE System experts, the Qbot malware has received one such major update, which has contributed to a recent spike of activity, especially after December 2015 and through early 2016.
This new version of Qbot embraces a new technique called polymorphism that Webroot experts have seen gain popularity during the past year.
BAE Systems experts say that Qbot uses a two-stage polymorphism process that generates unique malware samples for each computer the virus infects.
Qbot distributed via the RIG exploit kit
Most of the infections occur when users from these organizations visit websites that redirect them, through malvertising or social engineering tricks, to sites hosting the RIG exploit kit, a crimeware specialized in infecting less secure PCs with malware.
In this case, it's the Qbot malware, which, once downloaded on an infected computer, immediately tries to spread to nearby workstations.
To do this, Qbot uses network-shared folders. If these folders are password-protected, Qbot tries to steal credentials from Internet Explorer and the Windows Credential Manager. If these techniques fail, Qbot also comes with a list of common user and password combos, which it uses to mount brute-force attacks.
After it infects as many victims as possible, Qbot then contacts its C&C server, from where it receives updates every six hours. These updates, besides instructions on what to do, also contain new versions of the malware, generated via the two-stage polymorphism process that alters Qbot's structure, allowing it to avoid most antivirus software.
Most Qbot infections are found in the US public sector
BAE was alerted to this threat when one of its clients detected suspicious activity from its network. After the security firm's investigation, it turned out that over 500 computers were infected with Qbot.
A later DNS sinkholing exercise revealed to BAE researchers that Qbot's botnet manages connections to more than 54,000 infected PCs all over the globe.
"Qbot is designed with persistence and mass infection in mind, seen through its polymorphic capabilities and anti-VM checks," BAE's researchers explain. "We expect that Qbot will continue to be a potent threat over the coming months, facilitated by exploit kits to provide an initial infection, and automated spreading to gain maximum victim count."
"Whilst the current campaign has already gained media coverage, the malware itself continues to remain relatively under-reported within open source, despite already claiming a large victim pool in the two-to-three months it has been active," BAE researchers also noted.
For an in-depth technical write-up, we recommend reading BAE's The Return of Qbot whitepaper.

 14 DAY TRIAL //
14 DAY TRIAL //