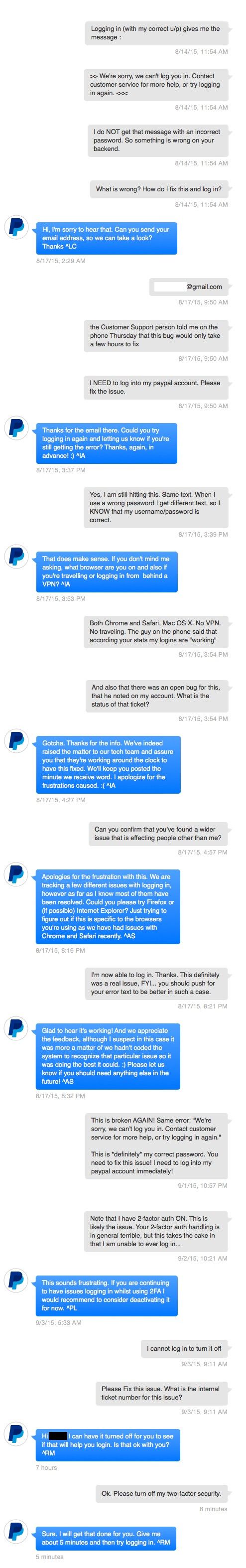
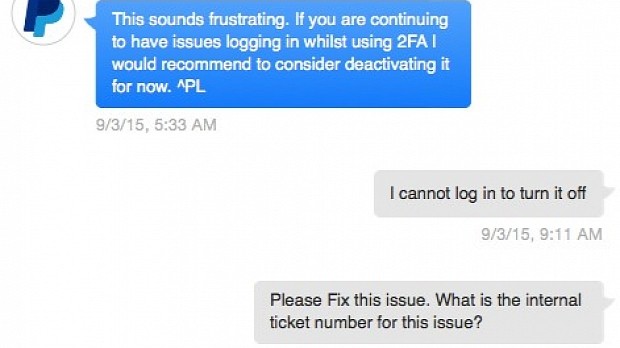
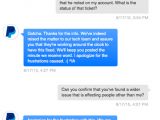
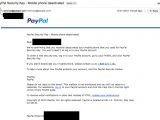
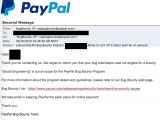
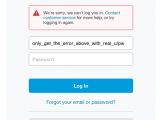
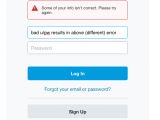
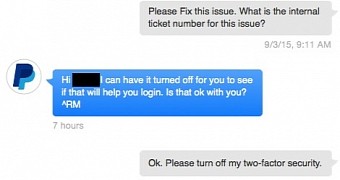
An anonymous user has posted some images on Imgur detailing how a PayPal customer support employee disabled two-factor authentication (2FA), one of the company's most advanced user protection systems, without verifying the user's identity with one single question.
Social engineering is one of the most encountered methods of compromising accounts, relying on basic human interaction, and on convincing or tricking other people into breaking normal security practices.
If you work for one of the biggest payment processing companies on the Internet and a random Twitter user convinces you to disable the two-factor authentication system for an account just by providing you with an email, that's a textbook "social engineering" case.
Below is the astonishing conversation the PayPal employee and the owner of the PayPal account had, along with email confirmation for the disabled account, and a reply from PayPal's Bug Bounty program, which stated that social engineering was not high on their list of "bugs."
True, it may not be a bug, but it's still a procedural flaw which needs to be fixed.
While everyone hates those lengthy barrages of security questions we are put through by bank employees when dealing with them on the phone, I'm willing to bet none of us will want them skipped.
Let's hope this was just a one-time incident for PayPal and the screengrabs of this conversation end up in a training manual for the company's customer support department.
 14 DAY TRIAL //
14 DAY TRIAL //