After DroidJack, AndroRAT, DarkComet, and njRAT, a new Android RAT, named OmniRAT, has surfaced on the black market. This RAT is new, having been created this year and being sold by a team of German developers.
RAT stands for Remote Access Trojan (some use the term Tool as well) and refers to a particular piece of malware that infects user computers via a client component, which then starts communicating with a server counterpart. This allows an attacker to steal data from a target, spy on the user, and even take control of the victim's device.
OmniRAT is 10 times cheaper than DroidJack
Unlike previous Android RAT kits, OmniRAT comes with built-in support for controlling desktops, something that its competitors don't have the ability to do. Additionally, also compared to its competition, OmniRAT is also ten times cheaper to purchase, being offered for sale at prices between $25 and $50 (€23 and €46).
Software like this is not illegal, mainly because it is also used by programmers and testers in their daily jobs. RATs become illegal when someone uses them for malicious purposes.
Around mid-August this year, Avast detected one of these malicious campaigns in action, one that involved a version of OmniRAT, spreading via SMS messages.
Attackers are distributing OmniRAT via SMS messages
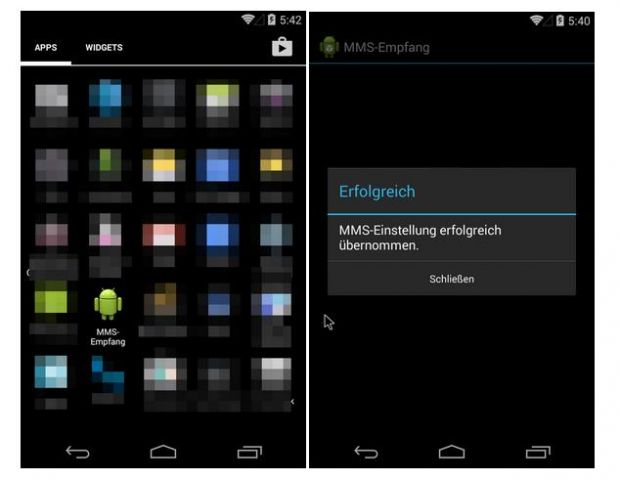
Victims were receiving a simple SMS message that was informing them that they received an MMS, but that it could not be sent to their phone because of the Stagefright vulnerability (exploitable via the phone's built-in MMS viewing library).
Instead, victims were asked to access the MMS via a bit.ly link in their browser. The page on which they landed asked users to enter a code sent via the SMS message, along with their phone number.
This operation starts the download of an Android app (.apk file) on the user's phone. If users are careless enough to open and install a random app they've been force-fed off the Internet, that app will prompt the user saying that their MMS settings have been "successfully modified" and that an "MMS Retrieve" icon has been added to their homescreen.
Paranoid users are safe from OmniRAT, careless users will surely be infected
As you can guess, launching this MMS Retrieve app installs OmniRAT, but not before the user is asked to give it all the necessary permissions, which are plenty and quite intrusive.
If users tend to ignore the permissions popup and just hit "Install" and "Next" without reading their content, OmniRAT will have full control over the device.
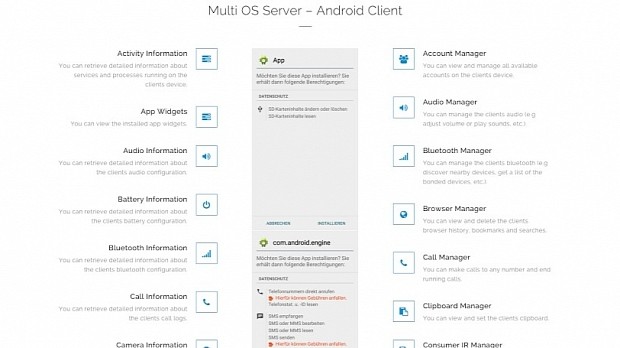
This includes making calls, sending SMS messages, recording audio, getting a list of all installed apps, accessing Web browsing history, accessing the contact list, executing shell commands, getting battery info, getting Bluetooth information, and many, many other more.
In the campaign Avast detected, data from infected devices was sent to a Russian domain, where the OmniRAT's server was located.
At the time Avast saw the first signs of OmniRAT, this video also popped up on YouTube. Enjoy!
 14 DAY TRIAL //
14 DAY TRIAL //