The Nigerian cyber-crime scene, famous for its Nigerian Prince and 419 scam tactics, has evolved to using malware and is now actively targeting enterprises and employing BEC (Business Email Compromise) techniques, a SecureWorks investigation has revealed.
For many years, the Internet has been plagued with massive spam floods, in most instances carrying emails from Nigerian cyber-crime crews that were trying to extort and fool home users into sending them money via various methods. Historically, these crews have been calling themselves "yahoo-yahoo boys," "yahoo boiz," or "G-boys."
As time passed and the Internet population got more educated, their tactics became known and entered the Internet lore. As such, a change was needed.
Nigerian scammers shift focus to businesses
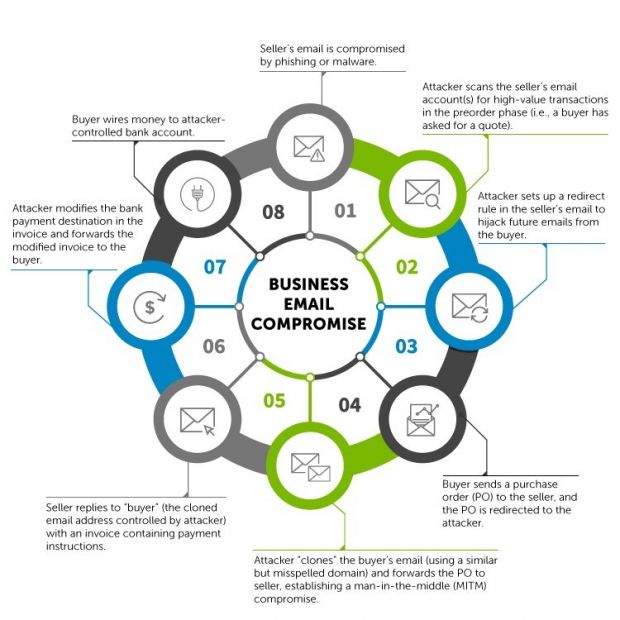
Riding the rising wave of BEC scams, Nigerian scam crews have shifted their focus towards businesses instead of home users. Using BEC (Business Email Compromise) and BES (Business Email Spoofing) tactics, these groups are targeting the email communications between companies, looking for orders and invoices.
The scammers compromise email servers or email accounts, search for ongoing business leads, and register look-alike domains in order to intervene as a middleman between those email exchanges.
Most of the time, they clumsily edit emailed PDF invoices, adding their bank account details instead of the correct one. They also send spoofed emails claiming to be one or another high-ranking exec inside a company, requiring an urgent payment. The first method seems to be more lucrative than the second since it's harder to spot.
WWG1 uses email bombs and RATs
SecureWorks says it discovered a group, which they named Wire-Wire Group 1 (WWG1) or Threat Group-2798 (TG-2798), actively targeting businesses.
This group uses commodity remote access trojans (RATs), which they email en masse to victims in a tactic called email bomb. The malware is used to infect targets, get control of their PCs, and gather intelligence. SecureWorks says the group is not particularly apt to deal with malware but has one member who handles this operation.
In fact, the group managed to infect one of their own computers, allowing SecureWorks experts who were investigating the RAT's server to discover details about their operations.
WWG1 has over 30 members
WWG1 consists of over 30 members, most of whom are from their late twenties up to their forties, operate from home, don't flaunt their wealth on social media, and are very active in their local churches.
This is the opposite of the image everyone had of the yahoo boyz in the past, namely college teens who operate from cyber-cafes and show off on social media.
In fact, most of the Nigerian BEC scammer gangs don't use the yahoo boyz term to describe themselves, but prefer expressions such as "wire-wire," "waya-waya," or "the new G-work."
What businesses should do, according to SecureWorks, is to implement 2FA for corporate and personal email accounts, inspect corporate email control panels for suspicious redirect rules, carefully review current and past wire transfers for the correct payment details, and use non-email channels to confirm wire transfers with their business partners.
To help enterprises targeted by this kind of BEC groups, the company has even published a tool that can analyze PDFs and highlight any later edits, such as new bank account numbers overlaid on top of the original document.

 14 DAY TRIAL //
14 DAY TRIAL //