New ransomware malware is targeting MacOS users. Called "Patcher," the new campaign uses BitTorrent distribution sites as the way into people's computers.
Security firm ESET rings the alarm about these patchers people are trying to download, which instead of the promised file actually contain the malware.
More specifically, when people try to download the patchers from torrent sites, there's only one ZIP file which contains the application bundle. According to the security firm, this particular ransomware was discovered in files that were supposed to fix Adobe Premiere Pro and Microsoft Office for Mac, but more could be out in the wild.
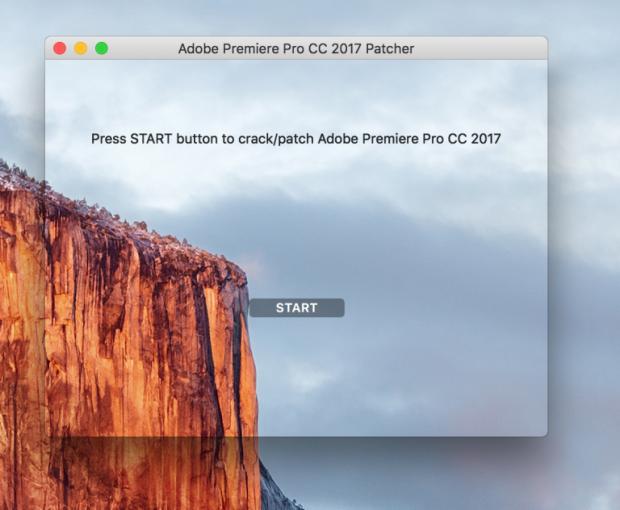
Don't hit "Start"
The application is poorly coded, the researchers state and indicate to one window that has a transparent background instead of the regular white backdrop. If the window is closed, it's impossible to reopen it, they add. If this is all you do, then there may still be hope for your files.
If you, however, tap the "Start" button in the window, say goodbye to your files because that's when the encryption process starts. A file called "README!.txt" is copied all around the user's directories, containing the ransomware instructions. Then, a random 25-character string is generated to use as the key to encrypt the files. All files make use of the same key. The files are enumerated with the "find" command line tool, and then the zip tool is used to store the file in an encrypted archive.
"Finally, the original file is deleted with rm and the encrypted file’s modified time is set to midnight, February 13th 2010 with the touch command. The reason for changing the file’s modified time is unclear. After the /Users directory is taken care of, it does the same thing to the mounted external and network storage found under /Volumes," ESET researchers explain.
No way to recover files
One big problem comes with this particular ransomware, however, and that's the fact that it's poorly coded and this makes it impossible for users to eventually get their data back. Why? Because there seems to be no code to communicate with any C&C server, which means the decryption keys can't be sent to the malware operators. Paying the ransom will not do anything to get people's files back.
The ransomware instructions ask victims to send 0.25 BTC to a certain address, which means unlocking your files might cost about $250 if you decide to pay the price. Paying more will get your files decrypted in record time, not the regular 24 hours.
The bitcoin address provided by the attackers features zero transactions at this moment, so they've yet to find any victims, which is great news.
 14 DAY TRIAL //
14 DAY TRIAL //