We're getting close to the end of the year, and annual reports are about to flood your news feeds. One of the first to come out is from Blue Coat, and it presents the top threat trends and infection sources for mobile devices.
While in 2014 the prime source of infection were mobile ads with a "market share" of 19.69%, in 2015, pornography apps and websites have managed to account for 36.13% of all infected mobile users.
This number is much greater than the 2013 value of 22.16%, when pornography websites also topped the list as the main source of infections on mobile devices.
Blue Coat says that, most of the time, infections come via malvertising attacks, and via websites that distribute pornography apps that bundle hidden trojans in their code.
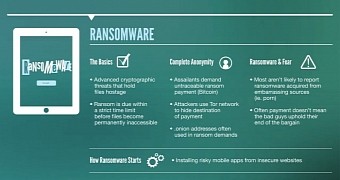
Ransomware is becoming a big problem on mobile devices
While the trend of using adult content to appeal to users is not something new, having previously wreaked havoc on desktop PCs for years, during 2015, Blue Coat has additionally noted an uptick in mobile ransomware.
In previous years, mobile ransomware was not quite such a problem, mainly due to the simple and unsophisticated level at which ransomware infections manifested themselves.
Most of them were quite easy to bypass and remove, but in recent months, after many years of hits&misses, coupled with advances in Android OS capabilities, today's world of mobile ransomware is as dangerous as the one you see on regular computers.
In recent months, security vendors and antivirus companies have started observing mobile ransomware with file encrypting capabilities, C&C server connections, rootkit-like persistence capabilities, and harder to remove lockscreens.
Using TOR to mask ransom demands
Put ransomware, pornography, and the Tor network together, and you have mobile threats as dangerous and as hard to track and remove as on desktops.
"Creators of mobile ransomware are also taking advantage of the Tor anonymity network to obscure the real destination of the ransom payment. It’s not uncommon to see “.onion” addresses used in ransom demands," say Blue Coat researchers. "Victims have very little time to get up to speed on the intricacies of Tor before the deadline to pay clicks away and their precious files are lost forever."
You can get Blue Coat's report from their website. A quick summary can be viewed in the infographic below.
 14 DAY TRIAL //
14 DAY TRIAL // 