To improve the efficiency of its campaigns, LemonDuck has refined and strengthened its techniques for attacking both Windows and Linux by focusing on earlier vulnerabilities and streamlining processes, according to The Hacker News.
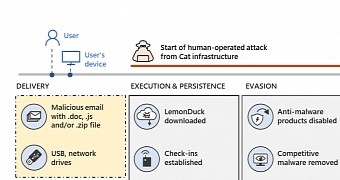
The malware known as LemonDuck, an active and robust malware renowned for its botnet and cryptocurrency mining targets, took on more sophisticated actions and intensified its operations, according to Microsoft. The latest version is able to eliminate security checks, spread through e-mails, move laterally, steal credentials, and drop out more tools for human-run operations.
The malware is known for its ability to spread rapidly across an infected network to facilitate information theft and convert machines into cryptocurrency mining bots by using computer resources to illegally mine cryptocurrency. Specifically, LemonDuck acts as a loader for follow-on attacks that involve stealing credentials and installing next-level implants that can serve as a gateway for a number of threats, the most important of which is ransomware.
Another notable tactic is the ability to "remove additional attackers from a compromised device by removing competing software and preventing new infections by fixing the vulnerabilities the attacker was able to access."
LemonDuck was used by cybercriminals in many countries around the world
Attacks using LemonDuck malware mostly targeted the manufacturing and IoT industries, with most encounters occurring in Russia, Korea, China, France, Germany, India, Canada, Vietnam, and the United States. Furthermore, Microsoft exposed the operations of a second entity, LemonCat, that makes use of LemonDuck to accomplish various goals.
The Cat attack architecture reportedly surfaced around January 2021 and eventually led to attacks that exploited vulnerabilities in Microsoft Exchange Server. Subsequent tampering with the use of Cat domains led to the installation of backdoors, credentials and data theft, as well as the deployment of malware, often a Windows Trojan dubbed Ramnit.
Microsoft went on to say that just because Cat infrastructure is used for more destructive assaults does not indicate that malware infections using Duck infrastructure are any less serious. Instead, this information gives crucial context for comprehending this threat: the same tools, access points, and procedures can be utilized at variable intervals, resulting in greater overall damage than previously anticipated.
 14 DAY TRIAL //
14 DAY TRIAL //