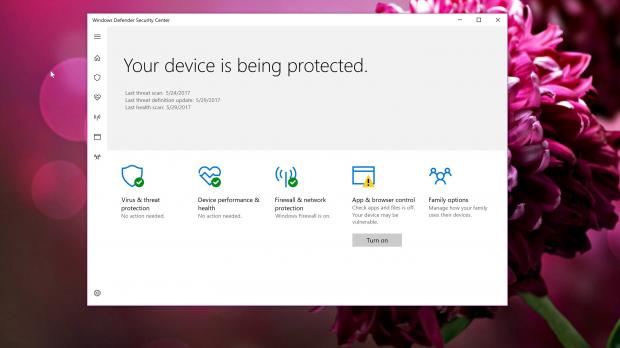
Microsoft rolled out a silent patch for a remote code execution flaw in the Malware Protection Engine, serving as the foundation of the company’s security software in Windows, including Windows Defender available by default in Windows 10.
Discovered on May 12 by Google Project Zero security researcher Tavis Ormandy, the flaw existed in the MsMpEng x86 emulator, which could be hijacked by attackers with a compromised executable file, mostly because it’s not sandboxed.
“MsMpEng includes a full system x86 emulator that is used to execute any untrusted files that look like PE executables. The emulator runs as NT AUTHORITY\SYSTEM and isn’t sandboxed. Browsing the list of win32 APIs that the emulator supports, I noticed ntdll!NtControlChannel, an ioctl-like routine that allows emulated code to control the emulator,” the security expert explains.
“Command 0x0C allows you to parse arbitrary-attacker controlled RegularExpressions to Microsoft GRETA (a library abandoned since the early 2000s)… Command 0x12 allows you to load additional ‘microcode’ that can replace opcodes… Various commands allow you to change execution parameters, set and read scan attributes and UFS metadata. This seems like a privacy leak at least, as an attacker can query the research attributes you set and then retrieve it via scan result,” he continued for users interested in more technical details.
“Extremely bad vulnerability”
Ormandy calls the security flaw a “potential extremely bad vulnerability,” but he notes that it’s not as hard to exploit as the one that he discovered earlier this month and was patched by Microsoft in record time.
On the other hand, this new security vulnerability was reported to Microsoft privately, and the company shipped a fix last week. In order to remain protected, users only need to have automatic updates turned on and run the latest version of Windows Defender with the newest virus definitions.
Microsoft is yet to provide a statement on this, but given that the patch has already been fixed, Redmond’s job here is complete and no further details are needed.
And yet, this security fix shows once again why it’s critical for users to keep automatic updates always enabled and to run the latest version of Windows 10. Microsoft delivers patches and updates as soon as they are ready, so by disabling automatic updates, it could take longer to deploy fixes, which in some cases could prove to be critical, especially with hackers continuously searching for this kind of flaws in the operating system.
 14 DAY TRIAL //
14 DAY TRIAL //