In its regular Patch Tuesday monthly security update, Microsoft fixed a series of issues in its operating systems but also included a patch for Silverlight, the company's Flash clone application platform.
According to Kaspersky, two of the company's security researchers, Costin Raiu and Anton Ivanov, uncovered a Silverlight zero-day bug in the 400GB of data dumped online after the Hacking Team breach in June 2015.
The two were initially put on the trail by an email included in the Hacking Team data, which was later published in an ArsTechnica article.
Hacker tried to sell the Silverlight zero-day to the Hacking Team
The email was from a Russian hacker named Vitaliy Toropov, who was writing to the Hacking Team, asking if they were interested in buying zero-days in applications like Flash, Silverlight, Java or Safari.
According to the published emails, Toropov revealed that he was in possession of a 2.5-year-old Silverlight zero-day, which also had the potential to remain undisclosed for a few more years.
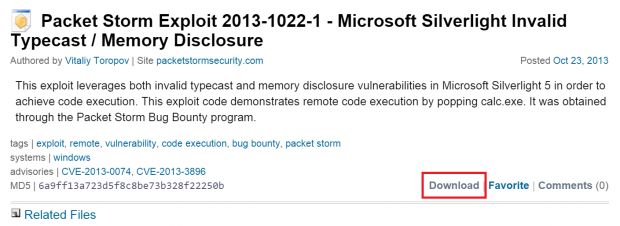
Kaspersky's researchers got to work and soon were able to find Silverlight exploit code credited to Toropov's name on the Packet Storm Security portal.
The zero-day bug was used in live attacks in November 2015
The two added the exploit code to Kaspersky's security products and waited for a warning to be triggered in its products if an attacker tried to use it. This happened on November 25, 2015.
According to Kaspersky, the file that triggered the security alert was compiled on July 21, 2015, just a few weeks after the Hacking Team data was dumped online.
When exploited via a Web browser, the bug allowed an attacker to gain the same privileges the user had on the infected computer. While not a dangerous threat on its own, the bug can be chained together with other zero-days and be used to carry out more dangerous, intrusive attacks.
"One of the biggest questions we have is whether this is Vitaliy Toropov’s Silverlight zero-day which he tried to sell to Hacking Team. Or is it a different one?" the Kaspersky researchers asked themselves. "Several things make us think it’s one of his exploits, such as the custom error strings. Of course, there is no way to be sure and there might be several Silverlight exploits out there."
While the researchers may not be sure that this is the exact zero-day that Toropov tried to sell to the Hacking Team, they are sure it's Toropov's work and that it's patched now, thanks to their investigative efforts and Microsoft's prompt security staff.

 14 DAY TRIAL //
14 DAY TRIAL //