Security studies are being released on a daily basis, and there's an industry trend that's been focused on raising awareness about data breaches.
One of the latest such reports comes from Intel Security and provides data gathered from 1,155 organizations around the world, all relating to data breaches, today's current security hot topic.
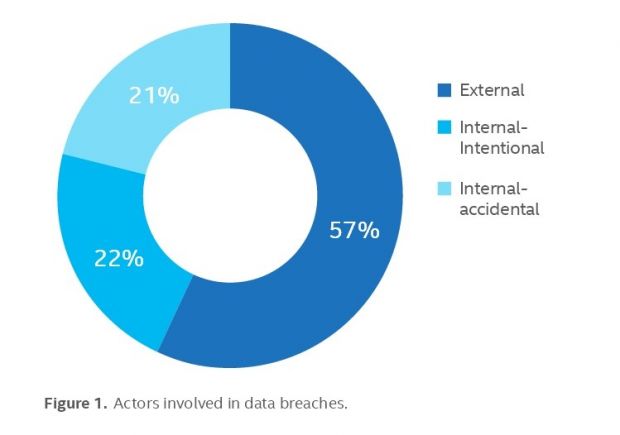
According to Intel, most data breaches occur because of external factors in 57% of the cases. When an internal factor is to blame, 21% of the breaches occur because of an accident, while 22% are intentional.
Attackers prefer customer and employee information over credit card details
In most of the data breaches, attackers are targeting customer and employee information, with less focus put on intellectual property and financial information.
In the majority of cases, both internal and external actors are targeting Microsoft Office files (Word, PowerPoint, Excel) above everything else, followed by CSV and plain text files (usually database dumps), PDFs, audio and video multimedia files, and XML data.
The funny thing is that, while most of us think of a complicated cyber-espionage or hacking attack when we say data breach, the Intel report confirms that in 40% of the cases the data is stolen along with the actual, physical device.
Lost or stolen laptops are one of the main reasons for data breaches
The favorite targets are laptops, tablets, and USB drives, followed by smartphones, printed documents, CDs/DVDs, microphones, webcams, and faxes.
In the cases where hackers decide to use digital avenues to hack into a company's network, they usually prefer Web protocols (like HTTP), followed by FTP, email, P2P, SSH, and VPN.
The Intel Grand Theft Data report also covers cloud infrastructures, seen in more and more companies each new year. According to their survey, one in three data breaches were recorded on a cloud server.

 14 DAY TRIAL //
14 DAY TRIAL //